FruityArmor APT group used recently patched Windows zero-day flaw
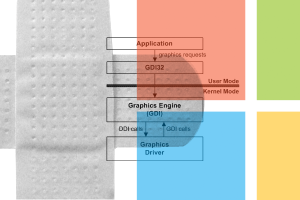 One of the four zero-day vulnerabilities Microsoft patched last week was being used by an APT group called FruityArmor to carry out targeted attacks, escape browser-based sandboxes, and execute malicious code in the wild.
One of the four zero-day vulnerabilities Microsoft patched last week was being used by an APT group called FruityArmor to carry out targeted attacks, escape browser-based sandboxes, and execute malicious code in the wild.
The vulnerability stemmed from the way a component, Windows graphics device interface, handled objects in memory. GDI is an application programming interface in Windows that helps apps that use graphics and formatted text on the video display and printer. Microsoft said in bulletin that an attacker could exploit the vulnerability multiple ways.
Read moreDXXD ransomware shows ransom note using Windows legal notice screen
 A new ransomware that goes by the name of DXXD uses the Windows Legal Notice screen to show a ransom note even before the user logs on his or her computer.
A new ransomware that goes by the name of DXXD uses the Windows Legal Notice screen to show a ransom note even before the user logs on his or her computer.
The Windows Legal Notice screen is an intermediary screen that appears before the Windows login form and, as its name hints, it's there for the purpose of showing various types of legal notices and other messages before a user can use the PC. This is the first time a ransomware author has used the Legal Notice screen to show a ransom note, but won't be the last. While users can dismiss the notice by pressing the "Ok" button, the screen does its job and gets the user's attention.
Read moreFastPOS malware abuses Windows Mailslots to steal POS data
 The group behind the FastPOS malware has updated their trojan with a new data exfiltration mechanism that abuses the Windows Mailslots mechanism to store data before exfiltration from infected systems.
The group behind the FastPOS malware has updated their trojan with a new data exfiltration mechanism that abuses the Windows Mailslots mechanism to store data before exfiltration from infected systems.
This new version of POS malware came to light this past summer when researchers discovered ads for it on underground carding forums. Analysis of the malware showed a new POS malware family that focused on speed and sacrificed stealth, an opposite approach to how most POS malware operate today. Trend Micro continued its analysis of this malware after the initial detection and discovered traces of FastPOS activity dating back to March 2015.
Read moreMicrosoft Windows could soon track everything you do on your PC
 Browsing through Microsoft patent library we often come across ideas which we wish they implemented, but which never made it to a product. Today we came across the opposite – an idea whose time we hope never comes.
Browsing through Microsoft patent library we often come across ideas which we wish they implemented, but which never made it to a product. Today we came across the opposite – an idea whose time we hope never comes.
The patent notes that efficient searching is enhanced if more information is available regarding the user intent, giving the example of someone doing a school report on dancing, and noting that despite the user having done some work already, when they hit the browser to search the search engine would not have any idea what the user is working on except for what they have typed into the search bar. People use multiple desktop applications in order to complete a single task.
Read moreRemote hacker steals Windows 10 logins in Safe Mode attack
 Security researcher Doron Naim has found an attack that abuses Windows 10's Safe Mode to help hackers steal logins. The Cyberark man says remote attackers need to have access to a PC before they can spring this trap, which involves rebooting a machine into Safe Mode to take advantage of the lesser security controls offered in that environment.
Security researcher Doron Naim has found an attack that abuses Windows 10's Safe Mode to help hackers steal logins. The Cyberark man says remote attackers need to have access to a PC before they can spring this trap, which involves rebooting a machine into Safe Mode to take advantage of the lesser security controls offered in that environment.
Once in Safe Mode, logins can be stolen and otherwise with defeated pass-the-hash lateral techniques can be used to compromise other networked machines. A fake login screen can be shown using a COM object technique to emulate a normal boot and cloak Safe Mode.
Read moreFantom Ransomware encrypts your files while pretending to be Windows update
 There’s yet another new type of ransomware out there. Fantom is a new form of the malicious virus that disguises itself as an important Windows update. Ransomware encrypts a victim’s files and holds them ransom for a fee — and cybercriminals are getting savvier in tricking people into clicking malicious links and downloading the virus.
There’s yet another new type of ransomware out there. Fantom is a new form of the malicious virus that disguises itself as an important Windows update. Ransomware encrypts a victim’s files and holds them ransom for a fee — and cybercriminals are getting savvier in tricking people into clicking malicious links and downloading the virus.
Fantom was discovered by Jakub Kroustek, a security researcher at AVG. He found that the culprits had actually gone to great lengths to disguise their work. The malicious file’s properties list details like Microsoft’s copyright and trademark information to make it appear legitimate.
Read morePokemon GO ransomware installs Windows admin backdoor account
 It was only a matter of time until some clever hacker decided to leverage Pokemon GO's huge success to create Pokemon-themed ransomware. The bad news is that the person who developed this new threat is not happy with just delivering a basic crypto-ransomware but is also interested in data exfiltration scenarios as well as creating a backdoor account on the infected devices.
It was only a matter of time until some clever hacker decided to leverage Pokemon GO's huge success to create Pokemon-themed ransomware. The bad news is that the person who developed this new threat is not happy with just delivering a basic crypto-ransomware but is also interested in data exfiltration scenarios as well as creating a backdoor account on the infected devices.
This new ransomware appears to be currently under development, gearing up for a larger distribution campaign. The person behind this ransomware is distributing the threat as a Windows executable called PokemonGo.exe, which includes an icon of a very adorable Pikachu.
Read more20-year-old Windows bug lets printers install malware
 For more than two decades, Microsoft Windows has provided the means for clever attackers to surreptitiously install malware of their choice on computers that connect to booby-trapped printers, or other devices.
For more than two decades, Microsoft Windows has provided the means for clever attackers to surreptitiously install malware of their choice on computers that connect to booby-trapped printers, or other devices.
The vulnerability resides in the Windows Print Spooler, which manages the process of connecting to available printers and printing documents. A protocol known as Point-and-Print allows people who are connecting to a network-hosted printer for the first time to automatically download the necessary driver immediately before using it. It works by storing a shared driver on the printer or print server and eliminates the hassle of the user having to manually download and install it.
Read moreTech support scammers take tips from ransomware to make you pay up
 Tech support scams are commonplace. You receive a cold call from someone pretending to be from Microsoft, they attempt to convince you that they have "scanned" your computer and there are viruses and all they need to do as part of this dedicated customer service is go in there and clean it up for you.
Tech support scams are commonplace. You receive a cold call from someone pretending to be from Microsoft, they attempt to convince you that they have "scanned" your computer and there are viruses and all they need to do as part of this dedicated customer service is go in there and clean it up for you.
As long as you hand over details of your account and your bank details, of course. Unfortunately, such scams remain lucrative, especially if some of the older generation or vulnerable people are targeted. Now cyberscammers have taken a tip or two from the rise of ransomware to make their schemes even more profitable.
Read moreWindows zero-day exposes companies to credit card data theft
 Some of the attacks launched in March by a financially-motivated threat actor against organizations in North America involved a zero-day privilege escalation vulnerability affecting Windows. According to FireEye, this sophisticated cybercrime group targeted more than 100 companies — mainly in the retail, hospitality and restaurant sectors.
Some of the attacks launched in March by a financially-motivated threat actor against organizations in North America involved a zero-day privilege escalation vulnerability affecting Windows. According to FireEye, this sophisticated cybercrime group targeted more than 100 companies — mainly in the retail, hospitality and restaurant sectors.
The attackers used spear-phishing emails and malicious macro-enabled Word documents to deliver PUNCHBUGGY, a DLL downloader that allowed them to interact with the compromised system and move laterally in the victim’s network.
Read moreAxarhöfði 14,
110 Reykjavik, Iceland















