Hackers made over $1.5m with new Android banking malware that turns into ransomware
 A new Android banking malware dubbed LokiBot comes with some ransomware capabilities and is being sold on the dark web for $2,000 worth of Bitcoins. Although LokiBot functions primarily as a banking Trojan, it can turn into a ransomware if attempts are made to disable the malware's admin rights or when victims try to remove it.
A new Android banking malware dubbed LokiBot comes with some ransomware capabilities and is being sold on the dark web for $2,000 worth of Bitcoins. Although LokiBot functions primarily as a banking Trojan, it can turn into a ransomware if attempts are made to disable the malware's admin rights or when victims try to remove it.
Once the ransomware feature is activated, LokiBot encrypts all of the victims' data. The malware is also capable of stealing victims' contacts, reading and sending SMS messages and locking out users from accessing their phones. LokiBot's main attack vector involves phishing overlays on numerous banking apps.
Read moreAnonymous hacks Spanish government websites in 'Free Catalonia' cyber campaign
 Digital activists linked to the Anonymous collective, a disparate cohort of hackers from around the world, have claimed responsibility for a fresh wave of cyberattacks against a number of Spanish government websites as part of a pro-Catalonia protest campaign.
Digital activists linked to the Anonymous collective, a disparate cohort of hackers from around the world, have claimed responsibility for a fresh wave of cyberattacks against a number of Spanish government websites as part of a pro-Catalonia protest campaign.
Multiple accounts with Anonymous' signature Guy Fawkes masks have been tweeting hashtags in recent weeks including #opCatalunya, #FreeCatalonia and #OpSaveCatalonia. They claimed to have taken several state websites offline. The website of Spain's Ministry of Public Works and Transport was hacked to display a "Free Catalonia" slogan.
Read moreGoogle offers bug bounty to clean up mobile apps
 Google is offering security experts a bounty to identify Android app flaws as the Alphabet Inc unit seeks to wipe out bugs from its Google Play store.
Google is offering security experts a bounty to identify Android app flaws as the Alphabet Inc unit seeks to wipe out bugs from its Google Play store.
Each flaw will score at least $1,000 under the program announced on Thursday to back up automated checks that have failed to block malware and other problems that security experts say infect the 8-year-old app store far more than Apple Inc’s rival App Store. Google will partner with HackerOne, a bug bounty program management website, to target a list of apps and flaws such as those that allow a hacker to redirect a user to a phishing website or infect a gadget with a virus.
Read more'All Wi-Fi networks' are vulnerable to hacking, security expert discovers
 The security protocol used to protect the vast majority of wifi connections has been broken, potentially exposing wireless internet traffic to malicious eavesdroppers and attacks, according to the researcher who discovered the weakness.
The security protocol used to protect the vast majority of wifi connections has been broken, potentially exposing wireless internet traffic to malicious eavesdroppers and attacks, according to the researcher who discovered the weakness.
Mathy Vanhoef, a security expert at Belgian university KU Leuven, discovered the weakness in the wireless security protocol WPA2, and published details of the flaw on Monday morning. “Attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted, this can be abused to steal sensitive information.” Vanhoef’s report said.
Read moreElite hackers: stealing NSA secrets is ‘child’s play’
 The NSA’s hackers have a problem. Last week, multiple outlets reported that its elite Tailored Access Operations unit—tasked with breaking into foreign networks—suffered another serious data breach.
The NSA’s hackers have a problem. Last week, multiple outlets reported that its elite Tailored Access Operations unit—tasked with breaking into foreign networks—suffered another serious data breach.
The theft of computer code and other material by an employee in 2015 allowed the Russian government to more easily detect U.S. cyber operations. It’s potentially the fourth large-scale incident at the NSA to be revealed in the last five years. Now, sources with direct knowledge of TAO’s security procedures in the recent past tell just how porous some of the defenses were to keep workers from stealing sensitive information.
Read moreBeware of sketchy iOS popups that want your Apple ID
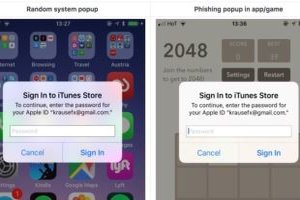 One of iOS' rougher edges are the popups it produces on a regular but seemingly random basis. These popups require users to enter their Apple ID before they can install or update an app or complete some other mundane task.
One of iOS' rougher edges are the popups it produces on a regular but seemingly random basis. These popups require users to enter their Apple ID before they can install or update an app or complete some other mundane task.
The prompts have grown so common most people don't think twice about them. Mobile app developer Felix Krause makes a compelling case that these popups represent a potential security hole through which attackers can steal user credentials. In a blog post published Tuesday, he showed side-by-side comparisons, pictured above, of an official popup produced by iOS and a proof-of-concept phishing popup.
Read moreHackers broke into Amazon cloud accounts to mine bitcoin
 Money may not grow on trees, but apparently, it can grow in Amazon Web Services (AWS).
Money may not grow on trees, but apparently, it can grow in Amazon Web Services (AWS).
A report from the security intelligence group RedLock found at least two companies which had their AWS cloud services compromised by hackers who wanted nothing more than to use the computer power to mine the cryptocurrency bitcoin. The hackers ultimately got access to Amazon's cloud servers after discovering that their administration consoles weren't password protected. "Upon deeper analysis, the team discovered that hackers were executing a bitcoin mining command from one of the Kubernetes containers," reads the RedLock report.
Read moreNorth Korean hackers 'stole US-South Korean war plans'
 North Korea has reportedly stolen a large amount of joint US-South Korean war plans, including details on how Kim Jong-un is to be assassinated during a potential conflict.
North Korea has reportedly stolen a large amount of joint US-South Korean war plans, including details on how Kim Jong-un is to be assassinated during a potential conflict.
Pyongyang’s secret army of hackers broke into the intranet of South Korea’s Defence Ministry in August and September last year and compromised a large cache of classified documents, Rhee Cheol-hee, a local politician said. Defence officials had previously admitted the breach but said no significant information had been stolen. However, Mr Rhee said the hackers had accessed OPLAN 5015, which is part of the most recent blueprint for war with North Korea that was drawn up by Seoul and Washington in 2015.
Read moreU.S. governors, hackers, academics team up to secure elections
 Hackers are joining forces with U.S. governors and academics in a new group aimed at preventing the manipulation of voter machines and computer systems to sway the outcome of future U.S. elections, a source familiar with the project said on Monday.
Hackers are joining forces with U.S. governors and academics in a new group aimed at preventing the manipulation of voter machines and computer systems to sway the outcome of future U.S. elections, a source familiar with the project said on Monday.
The anti-hacking coalition’s members include organizers of last summer’s Def Con hacking conference in Las Vegas, the National Governors Association and the Center for Internet Security, said the source, who asked not to be identified ahead of a formal announcement due to be made on Tuesday. The Washington-based Atlantic Council think tank and several universities are also part of the project, the source said.
Read moreRussian hackers reportedly stole NSA cyber defense material
 Russian hackers stole documents detailing how US agencies defend their networks against cyberattacks, how they breach foreign networks and the computer code they use to do so.
Russian hackers stole documents detailing how US agencies defend their networks against cyberattacks, how they breach foreign networks and the computer code they use to do so.
The stolen files were identified through Kaspersky security software used by an NSA contractor that had taken classified material from the NSA and saved it on his computer. The theft, discovered last spring, occurred in 2015 and those familiar with the incident told that having this information could help inform Russian officials how to protect their networks against the NSA and possibly how to break into US networks.
Read moreAxarhöfði 14,
110 Reykjavik, Iceland















