New IcedID trojan targets US banks
 Researchers are warning users about a wave of recent attacks targeting U.S. financial institutions that leverage a new banking Trojan dubbed IcedID.
Researchers are warning users about a wave of recent attacks targeting U.S. financial institutions that leverage a new banking Trojan dubbed IcedID.
The IcedID Trojan was spotted in September. They said the Trojan has several standout techniques and procedures, such as the ability to spread over a network and the ability to monitor a browser’s activity by setting up a local proxy for traffic tunneling. “At this time, the malware targets banks, payment card providers, mobile services providers, payroll, webmail and e-commerce sites in the U.S.,” researchers wrote in a report released Monday explaining the discovery.
Read moreGroup uses SEO to poison Google search results with links to banking trojan
 When you think you've seen it all, malware authors always find a way to impress you. Today's "that's clever!" moment comes courtesy of a criminal group that's been spreading a new version of the Zeus Panda banking trojan since June, this year.
When you think you've seen it all, malware authors always find a way to impress you. Today's "that's clever!" moment comes courtesy of a criminal group that's been spreading a new version of the Zeus Panda banking trojan since June, this year.
Instead of relying on old techniques of malvertising and spam campaigns, this group has taken a novel approach, never before seen in the distribution of banking trojans. Black-hat SEO, for the win! This Zeus Panda group decided to rely on a network of hacked websites, on which they inserted carefully chosen keywords in new pages or hid the keywords inside existing pages.
Read moreCryptoShuffler: Trojan stole $140,000 in Bitcoin
 Imagine that one day you decide to use Bitcoin to pay for, say, a pizza. You copy the wallet address from the pizzeria’s website, enter the required amount, and click the Send button.
Imagine that one day you decide to use Bitcoin to pay for, say, a pizza. You copy the wallet address from the pizzeria’s website, enter the required amount, and click the Send button.
The transfer goes through, but the pizza doesn’t arrives. The pizzeria owners say they never received the payment. What’s going on? Don’t get mad at the pizza guys — it’s all down to CryptoShuffler. Unlike cryptoransomware, this Trojan avoids flashy effects, instead doing its best to slip under the radar. It resides quietly in the computer’s memory and monitors the clipboard — the temporary storage area for cut/paste operations.
Read moreHackers made over $1.5m with new Android banking malware that turns into ransomware
 A new Android banking malware dubbed LokiBot comes with some ransomware capabilities and is being sold on the dark web for $2,000 worth of Bitcoins. Although LokiBot functions primarily as a banking Trojan, it can turn into a ransomware if attempts are made to disable the malware's admin rights or when victims try to remove it.
A new Android banking malware dubbed LokiBot comes with some ransomware capabilities and is being sold on the dark web for $2,000 worth of Bitcoins. Although LokiBot functions primarily as a banking Trojan, it can turn into a ransomware if attempts are made to disable the malware's admin rights or when victims try to remove it.
Once the ransomware feature is activated, LokiBot encrypts all of the victims' data. The malware is also capable of stealing victims' contacts, reading and sending SMS messages and locking out users from accessing their phones. LokiBot's main attack vector involves phishing overlays on numerous banking apps.
Read moreTrickbot malware now targets US banks
 The Trickbot banking Trojan is now targeting U.S. banks in new spam campaigns fueled by the prolific Necurs botnet. The malware has grown more potent with the introduction of a customized redirection method as part of its attacks.
The Trickbot banking Trojan is now targeting U.S. banks in new spam campaigns fueled by the prolific Necurs botnet. The malware has grown more potent with the introduction of a customized redirection method as part of its attacks.
IBM X-Force and Flashpoint both recently spotted new Trickbot activity. According to the researchers, spam campaigns have been active over the past several months, with the latest Trickbot attack reported earlier this week. While Flashpoint focused on the U.S. as targets, IBM focused on the redirection attacks used to steal login details, personally identifiable information and financial authentication codes.
Read moreTrickBot targets payment processors, CRM providers
 Banking Trojan TrickBot is no longer hitting only banks and financial institutions, but also added payment processing and Customer Relationship Management (CRM) providers to its list of targets.
Banking Trojan TrickBot is no longer hitting only banks and financial institutions, but also added payment processing and Customer Relationship Management (CRM) providers to its list of targets.
Supposedly developed by the same gang that previously operated the Dyre Trojan, TrickBot was first spotted in the summer of 2016, and initially detailed in October. By November, the malware was being used in widespread infection campaigns in the UK and Australia, and popped up in Asia the next month. Earlier this year, it started targeting the private banking sector. The 26 active TrickBot configurations observed in May 2017 were targeting banks.
Read moreZtorg Trojan: Infect yourself for 5 cents
 A lot of ads on the Internet promote easy ways to earn money. They tend to lead to fishy places — say, a post from an alleged mother of three who stays at home, earning several thousand dollars a day, and says you can do the same.
A lot of ads on the Internet promote easy ways to earn money. They tend to lead to fishy places — say, a post from an alleged mother of three who stays at home, earning several thousand dollars a day, and says you can do the same.
But there are other ways to earn some easy money, too, that may seem much more plausible. For example, some services offer to pay you for installing apps. The money amounts to pocket change, but the work is pretty effortless. This kind of scheme is especially popular among children — install 50 apps and get a $2.50 to buy some gear for your favorite character in an online game.
Read moreBankBot malware targeting hundreds of Android apps sneaks onto Google Play Store
 In January, security researchers warned that Android users may soon face a spike in malware attacks after the source code of a banking Trojan leaked online. Now, confirming the fears, Google is taking action after sneaky malware crept onto its official app store.
In January, security researchers warned that Android users may soon face a spike in malware attacks after the source code of a banking Trojan leaked online. Now, confirming the fears, Google is taking action after sneaky malware crept onto its official app store.
On 17 April the strain, dubbed "BankBot", was discovered in an application called "HappyTimes Videos" on Google's Play Store. In addition, experts from Securify, a Dutch cybersecurity firm, recently found another infected app there, titled "Funny Videos 2017". The Trojan is able to pose as legitimate services, mostly banks and financial institutions.
Read moreEwind Android adware is actually a full-fledged Trojan
 Palo Alto Networks researchers have analyzed a string of legitimate-looking Android apps and have discovered that the adware included in them has the potential to do much more than just show ads.
Palo Alto Networks researchers have analyzed a string of legitimate-looking Android apps and have discovered that the adware included in them has the potential to do much more than just show ads.
Variants of the Ewind adware/malware are usually packaged in popular game and social media apps such as GTA Vice City, Minecraft – Pocket Edition, VKontakte, but also in many mobile security apps such as AVG cleaner and Avast! Ransomware Removal. And these apps are offered for download on well-established online Android app stores catering Russian-speaking users. The adware Trojan in fact potentially allows full remote access to the infected device.
Read moreHackers using fake cellphone towers to spread Android banking trojan
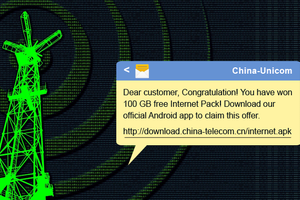 Chinese Hackers have taken Smishing attack to the next level, using rogue cell phone towers to distribute Android banking malware via spoofed SMS messages.
Chinese Hackers have taken Smishing attack to the next level, using rogue cell phone towers to distribute Android banking malware via spoofed SMS messages.
SMiShing — phishing attacks sent via SMS — is a type of attack wherein fraudsters use number spoofing attack to send convincing bogus messages to trick mobile users into downloading a malware app onto their smartphones or lures victims into giving up sensitive information. Security researchers have uncovered that Chinese hackers are using fake base transceiver stations to distribute "Swearing Trojan," an Android banking malware that once appeared neutralized after its authors were arrested in a police raid.
Read moreAxarhöfði 14,
110 Reykjavik, Iceland















