Just-released WordPress 0day makes it easy to hijack millions of websites
The WordPress content management system used by millions of websites is vulnerable to two newly discovered threats that allow attackers to take full control of the Web server.
 Attack code has been released that targets one of the latest versions of WordPress, making it a zero-day exploit that could touch off a series of site hijackings throughout the Internet.
Attack code has been released that targets one of the latest versions of WordPress, making it a zero-day exploit that could touch off a series of site hijackings throughout the Internet.
Both vulnerabilities are known as stored, or persistent, cross-site scripting (XSS) bugs. They allow a hacker to inject code into the HTML content received by administrators who maintain the website. Both attacks work by embedding malicious code into the comments section that appear by default at the bottom of a WordPress article post or blog. From there, attackers can change passwords, add new administrators, or take just about any other action legitimate admins can perform. The most serious of the two vulnerabilities is in WordPress version 4.2 because as of press time there is no patch.
The exploit works by posting some simple JavaScript code as a comment and then adding a massive amount of text—about 66,000 characters or more than 64 kilobytes worth. Once the comment is processed by someone logged in with WordPress administrator rights to the site, the malicious code will be executed with no outward indication that an attack is under way. By default, WordPress doesn't automatically publish comments to a post unless the user has already been approved by an administrator. Attackers can work around this limitation by posting a benign comment that gets approved. By default, subsequent comments from that person will be automatically approved and published to the same post.
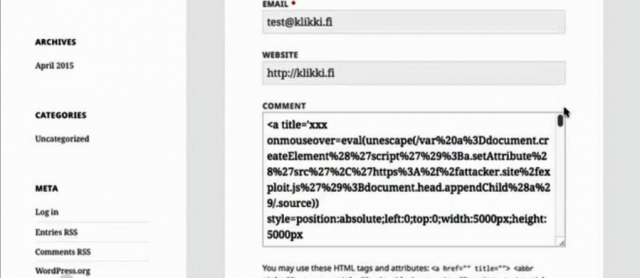
"If triggered by a logged-in administrator, under default settings the attacker can leverage the vulnerability to execute arbitrary code on the server via the plugin and theme editors," Jouko Pynnönen, a researcher with Finland-based security firm Klikki Oy, wrote. "Alternatively the attacker could change the administrator's password, create new administrator accounts, or do whatever else the currently logged-in administrator can do on the target system."
Klikki Oy has published a proof-of-concept attack code that looks like this: <a title='x onmouseover=alert(unescape(/hello%20world/.source)) style=position:absolute;left:0;top:0;width:5000px;height:5000px AAAAAAAAAAAA [64 kb] ...'>
Here's a video of the proof-of-concept attack in progress:
The attack is similar to one disclosed last week by security researcher Cedric Van Bockhaven. That attack also embedded malicious comments into comments that were executed when viewed by admins. The underlying vulnerability was fixed with last week's release of WordPress 4.2. A swarm of WordPress plugins were also recently updated to kill XSS vulnerabilities.
At the moment, there's no fix for the most recently disclosed bug. Once a patch is available, WordPress admins should install it right away. In the meantime, they should consider disabling comments or installing a comment plugin such as Akismet to mitigate exploits. Earlier this year, the US Federal Bureau of Investigation (FBI) just released a public service announcement (PSA) to the public about a large number of websites being exploited and compromised through WordPress plugin vulnerabilities.
Axarhöfði 14,
110 Reykjavik, Iceland














