How apps track your location without asking for permission
It’s common sense for Android users to check the permission list before installing an app. If the app asks for access to SMS, your contacts list or location, you know it may disclose your privacy and security.
 What if a game app only asked for the wifi_status permission? You might install it with ease – and unknowingly have enabled 3rd parties to track your location!
What if a game app only asked for the wifi_status permission? You might install it with ease – and unknowingly have enabled 3rd parties to track your location!
The Android LocationManager was considered to be the only way to acquire the location data, and required a user’s approval on the ACCESS_COARSE_LOCATION and ACCESS_FINE_LOCATION permissions. However, researchers at the Technical University of Denmark have discovered a covert channel to locate and track a user without permission by using the latent location signal disclosed by wifi scanning. Android has opened wifi status data to developers.
The only permission needed for developers is ACCESS_WIFI_STATE, which is common and considered low risk (vs. privacy-sensitive ACCESS_COARSE_LOCATION). Information now accessible to an Android developer includes:
- Scanned SSID list
- Scanned BSSID list
- Signal strength for scanned list
- IP Address for connected AP
Note that these metrics are accessible even with system wifi and location disabled! The code can be found here. A phone can be easily tracked with the BSSID and signal strength data.
What is BSSID?
BSSID is short for basic service set identification, which is the “MAC address” of the wireless access point. It is generated by combining the 24 bit Organization Unique Identifier. In short, BSSID is the unique fingerprint for a wifi access point, unlike the SSID which is human readable and can be duplicated.
If we can acquire a list of nearby BSSIDs, while having the wifi Access Points’ (AP) locations, we could locate the user in a small area – as most of the wifi APs are stable and cannot broadcast further than 100m (research shows only 5% of them are mobile APs such as personal devices). Also, by using the real-time signal strength data, we will be able to estimate the user’s moving track.
Next question: How many BSSIDs have known locations? Many, if not most are available, through a variety of services, through API queries. The website wigle.net claims to have 195,741,189 wifi hotspots’ location data:
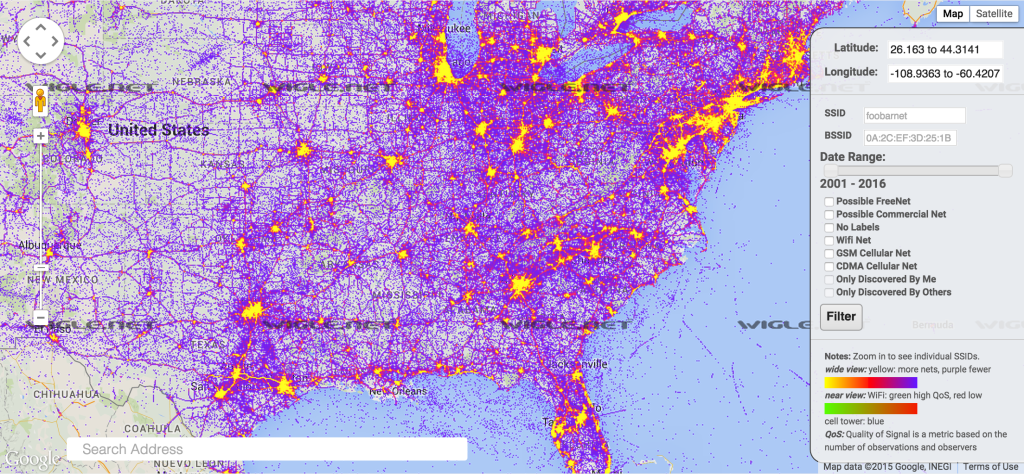
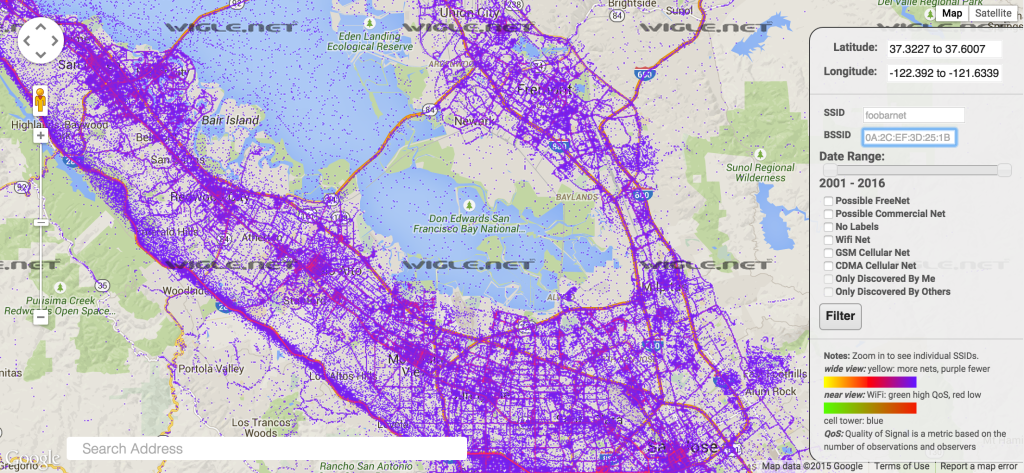
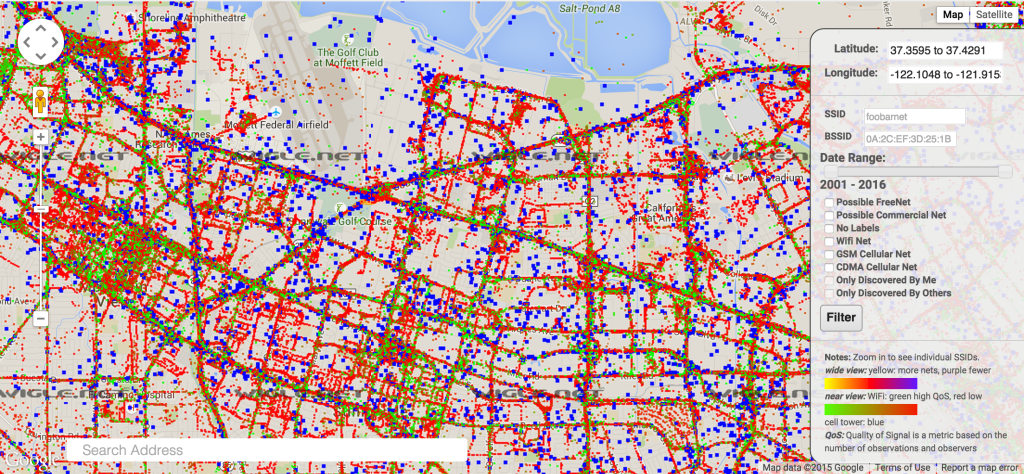
Living in the civilized world, could you escape such a web?
In the original paper, “Tracking Human Mobility using WiFi signalsz”, the authors highlight an example of following a user’s movement, tracking between home, 2 offices and a market, using the data from only 8 wifi access points:
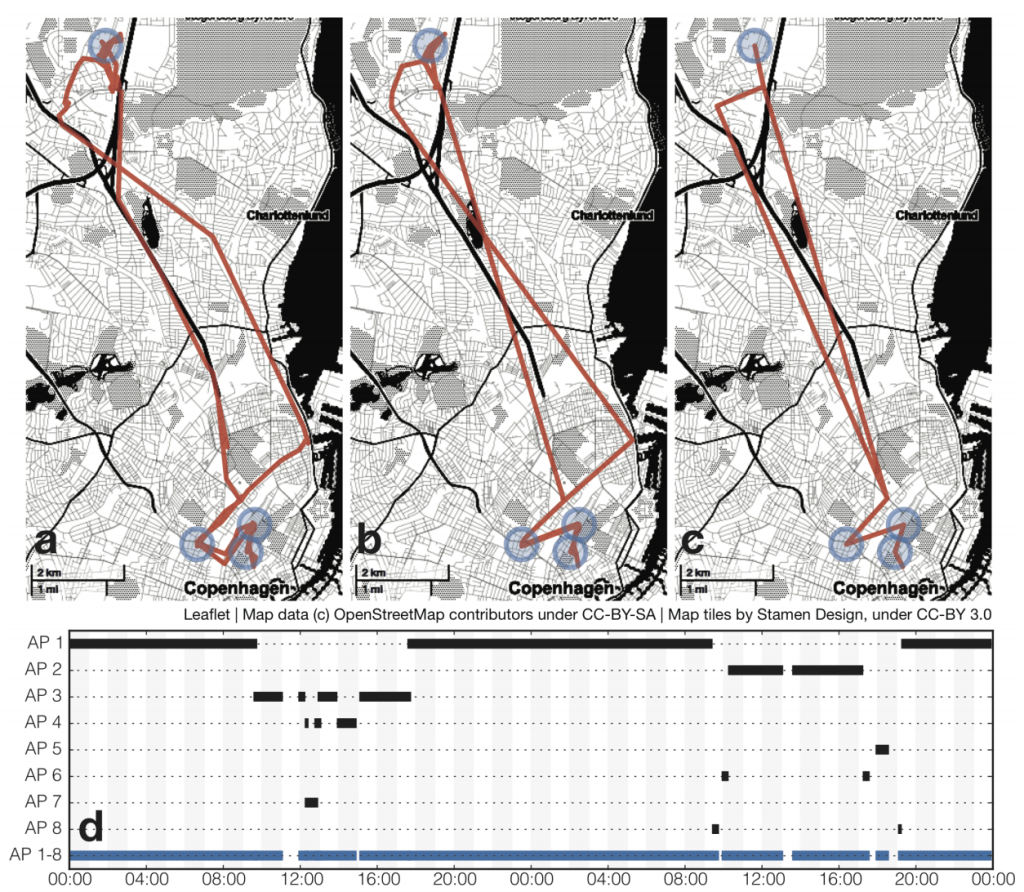
They also published a PoC app”WiFi Watchdog” on Google Play, I tried it and it was surprisingly accurate even though this app was granted no location permissions!
The same method also applies to iOS, which has greater user location data privacy protection. Nonetheless, iOS still allows acquiring the current connected wifi BSSID.
A user can deny the location requests on an iOS device at will. However, an app using wifi BSSID can still get a user’s static location without asking. Our research team is working on coverage of this covert channel privacy violation. Earlier the experiment at Carnegie Mellon University showed that smartphones spy on your location every three minutes. When people learn exactly how many times these apps share private information they rapidly act to limit further sharing. It means that mobile security isn’t on the highest level.
Axarhöfði 14,
110 Reykjavik, Iceland














