Parrot drones easily taken down or hijacked
In two separate presentations at Def Con in Las Vegas last weekend, security experts demonstrated vulnerabilities in two consumer drones from Parrot.
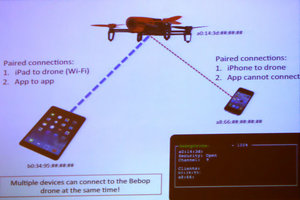 The simplest of the attacks could make Parrot drones, including the company's Bebop model, fall from the sky with a keystroke.
The simplest of the attacks could make Parrot drones, including the company's Bebop model, fall from the sky with a keystroke.
In a live demonstration at Def Con's Internet of Things Village, Ryan Satterfield of the security consulting firm Planet Zuda demonstrated a takedown of a Parrot A.R.Drone by exploiting the drone's built-in Wi-Fi and an open telnet port on the drone's implementation of the BusyBox real-time operating system. Connecting to the drone gave him root access to the controller, and he was able to kill the processes controlling flight — causing the drone to drop to the ground. In a session at DEF CON on August 9, researcher Michael Robinson, a security analyst and adjunct professor at Stevenson University in Maryland and George Mason University in Northern Virginia, dove further into the vulnerabilities of Parrot's drones, discussing his research on the Bebop drone in a session entitled, "Knocking My Neighbor's Kid's Cruddy Drone Offline."
Robinson noted that because of the Parrot's open Wi-Fi connection, it would allow anyone with the free Parrot app on a mobile device to pair with the drone in-flight. Using a Wi-Fi "de-auth" attack, he was able to disconnect the control app on the operator's device and take control with the app from another while the operator of the original controlling device attempted to re-establish a Wi-Fi connection. The new pilot could then simply fly the drone wherever he desired. Robinson warned anyone who planned to take over someone else's Parrot drone that the mobile app left forensic artifacts on mobile devices — including the serial number of the drone.
Like Satterfield, Robinson found that there was an open telnet port on the Bebop — and that this was a widely-known "feature" of the drone mentioned in forums by individuals who had used the vulnerability to hack the drone's performance and add new features to the small unmanned aircraft. (Some Parrot drone owners have used the feature to upgrade the Wi-Fi security of their drones to WPA-2 instead of the default open access). Killing flight processes didn't just make the Bebop drop to the ground, however—in an indoor test, Robinson said the drone suddenly lurched off like a projectile as it ungracefully shut down, slamming into a kitchen appliance.
Robinson also found that the Bebop also uses an open FTP server to transfer pictures and video back to the user. That means that anyone could remotely access, remove and replace media files on the Parrot drone. And if there was interference with the GPS signal received by the Bebop — say, from (illegal) GPS jammers — the drone's return-home function failed even when GPS signal returned.
Both Satterfield and Robinson said that they had contacted Parrot about the vulnerabilities, and that the company had said it was aware of them. It's not clear whether Parrot intends to fix them or not. Ars attempted to reach Parrot for comment, but we have not yet received a response.
Robinson also tested the security of the more expensive DJI Phantom III drone, with somewhat different results. The Phantom uses radio controls rather than Wi-Fi, so it was not vulnerable to hijacking. GPS interference caused problems for the return-home function and also, strangely, made video return from the Phantom unstable. And magnetic field interference could throw off the drone's internal magnetic compass, causing it to not take off; Robinson was unable to test the effects of magnetic interference in flight.
Axarhöfði 14,
110 Reykjavik, Iceland














