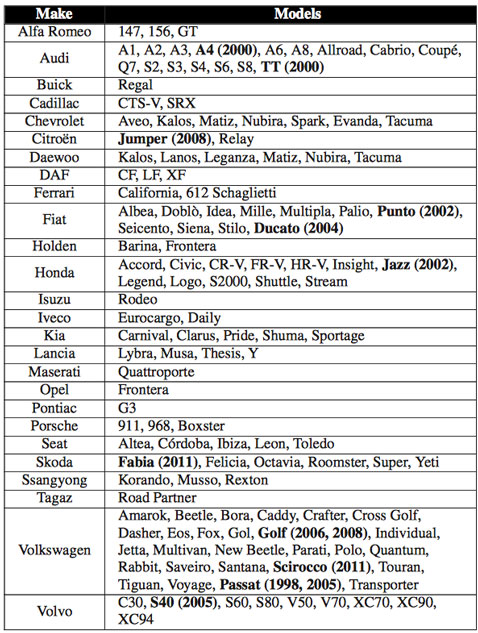
Security flaw affecting more than 100 car models
Since 2012, a trio of European researchers knew that the Megamos Crypto transponder sports vulnerabilities that can be exploited by attackers to start the cars without needing to have the key (i.e. the passive RFID tag embedded in it).
 They managed to reverse-engineer all proprietary security mechanisms of the transponder, including the cipher and the authentication protocol, and have devised three practical attacks that allowed them to recover the 96-bit transponder secret key.
They managed to reverse-engineer all proprietary security mechanisms of the transponder, including the cipher and the authentication protocol, and have devised three practical attacks that allowed them to recover the 96-bit transponder secret key.
One of these attacks allowed them to recover the key and start the engine with a transponder emulating device in just half an hour. And another is very hard to mitigate if the attacker has access to both the car and the transponder for a period of time (e.g., car rental, valet parking). "It is also possible to foresee a setup with two perpetrators, one interacting with the car and one wirelessly pickpocketing the car key from the victims pocket," they noted. "Our attacks require close range wireless communication with both the immobilizer unit and the transponder."
So, how come we're hearing about this problem only now?
Well, when the researchers first tried to present their findings at the 22nd USENIX Security Symposium in 2013, they were prevented from doing so by Volkswagen, who took them to court and won an injunction by the UK High Court of Justice prohibiting them from publishing key sections of the paper. Two years later, the injunction was lifted, and they finally had the opportunity to present their work on the at the 24th USENIX Security Symposium held last week in Austin, Texas.
"Although two years have passed, this work remains important and relevant to our community," Sam King, USENIX Security ’13 Program Chair, and Casey Henderson, USENIX Executive Director, noted in a foreword added to the paper, which has been amended to omit a crucial sentence that could help non-technical attackers work out how to execute the attacks. “This is a great example of what happens when you take an interface that was designed for local access and connect it to the wider Internet," commented Good Technology’s CTO, Nicko van Someren.
"Increasingly, in the rush to connect ‘Things’ for the Internet of Things, we find devices that were designed with the expectation of physical access control being connected to the Internet, the Cloud and beyond. If the security of that connection fails then the knock-on effects can be dire and potentially even fatal.” Car hacking has become an especially hot topic lately, as security researchers have turned their sights on testing automotive computers for vulnerabilities.
Earlier this year BT has launched a new security service developed to test the exposure of connected vehicles to cyber-attacks and help all market players develop security solutions, and initiatives like I Am The Cavalry have been encouraging the automotive industry to commit to cyber safety. NCC experts said that several car infotainment systems were vulnerable to a hack attack that could potentially put lives at risk.
Axarhöfði 14,
110 Reykjavik, Iceland














