Russian financial cybercrime: how it works
The Russian-language cybercrime market is known all over the world. By ‘Russian-language market’ we mean cybercriminals who are citizens of the Russian Federation and some former USSR countries, predominantly Ukraine and the Baltic states.
 Why is this market known worldwide? There are two main factors: the first of these is frequent global media coverage of the activity of Russian-language cybercriminals.
Why is this market known worldwide? There are two main factors: the first of these is frequent global media coverage of the activity of Russian-language cybercriminals.
The second is the open accessibility of online platforms used by the cybercriminal community for communications, promoting a variety of “services” and “products” and discussing their quality and methods of application, if not for making actual deals. Over time, the range of “products” and “services” available through this underground market has evolved, becoming more focused on financial attacks, and with an ever-increasing level of sophistication. One of the most common types of cybercrime was (and still is) the turnover of stolen payment card data.
With the emergence of online stores and other services involving e-payment transactions, DDoS-attacks and financial cybercrime have become especially popular with the fraudsters whose main targets are users’ payment data or the theft of money directly from user accounts or companies. Attacks on users’ and companies’ e-wallets were initiated by the Trojan ibank in 2006; then came ZeuS (2007) and SpyEye (2009) followed by the groups Carberp (2010) and Carbanak (2013). And this list is incomplete; there are more Trojans out there, used by criminals to steal users’ money and data.
With online financial transactions becoming more common, the organizations supporting such operations are becoming more attractive to cybercriminals. Over the last few years, cybercriminals have been increasingly attacking not just the customers of banks and online stores, but the enabling banks and payments systems directly. The story of the Carbanak cybergroup which specializes in attacking banks and was exposed earlier this year by Kaspersky Lab is a clear confirmation of this trend.
Kaspersky Lab security experts have been monitoring the Russian hacker underground since it first emerged. Kaspersky Lab regularly issues reports on financial cyber-threats which track changes in the number of financial malware attacks carried out over time. Information on the number of attacks may indicate the extent of the problem but does not reveal anything about who creates them and how. We hope that our review will help to shed light on this aspect of financial cybercrime. Between 2012-15, law enforcement agencies arrested over 160 Russian-speaking cybercriminals.
The data presented in this article is compiled from dozens of investigations that Kaspersky Lab experts have participated in over the last few years, as well as their many years’ experience observing the Russian cybercrime market.
Situation overview
According to Kaspersky Lab, between 2012 and 2015, law enforcement agencies from a number of different countries, including the United States, Russia, Belarus, Ukraine and the EU arrested over 160 Russian-speaking cybercriminals who were members of small, medium-sized and large criminal groups. They were all suspected of being engaged in stealing money using malware.
The total damage resulting from their worldwide activity exceeded $790 million dollars. (This estimate is based both on the analysis of public information about the arrests of people suspected of committing financial cybercrime in the period between 2012 and 2015 and on Kaspersky Lab’s own data.) Of this sum, about $509 million dollars was stolen outside the borders of the former USSR. Of course, this figure only includes confirmed losses, the details of which were obtained by law enforcement authorities during the investigation. In reality, cybercriminals could have stolen a much larger amount.
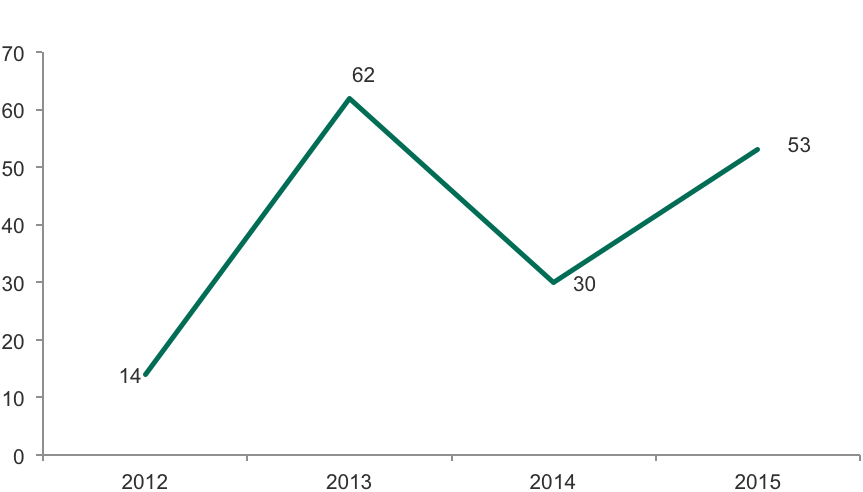
The number of arrests of Russian-speaking cybercriminals as officially announced during the period 2012 to 2015
Since 2013, Kaspersky Lab’s Computer Incidents Investigation team has participated in the investigation of more than 330 cybersecurity incidents. More than 95% of these were connected with the theft of money or financial information.
Although the number of arrests of Russian-language criminals suspected of financial cybercrime increased significantly in 2015 compared with the previous year, the cybercriminal market is still “crowded.”
According to Kaspersky Lab experts, over the last three years Russian-language cybercrime has recruited up to a thousand people. These include people involved in the creation of infrastructure, and writing and distributing malware code to steal money, as well as those who either stole or cashed the stolen money. Most of those arrested are still not in prison.
We can calculate fairly precisely the number of people who make up the core structure of an active criminal group: the organizers, the money flow managers involved in withdrawing money from compromised accounts and the professional hackers. Across the cybercriminal underground, there are only around 20 of these core professionals. They are regular visitors of underground forums, and Kaspersky Lab experts have collected a considerable amount of information that suggests that these 20 people play leading roles in criminal activities that involve the online theft of money and information.
The exact number of groups operating across Russia and its neighboring countries is unknown: many of those involved in criminal activities participate in several thefts and then, for various reasons cease their activity. Some participants of known but apparently disbanded groups continue their criminal activities as part of new groups.
Kaspersky Lab’s Computer Incidents Investigation Department can now confirm the activity of at least five major cybercriminal groups specializing in financial crimes. These are the groups whose activities have been monitored by the company’s experts over the last few years. All five groups came to the attention of the company’s experts in 2012-2013, and are still active. They each number between ten and 40 people. At least two of them are actively attacking targets not only in Russia but also in the USA, the UK, Australia, France, Italy and Germany.
Since the investigation into these groups has not been completed, it is not possible to publish more detailed information on the activities of these groups. Kaspersky Lab continues to investigate their activity and is cooperating with the law enforcement agencies of Russia and other countries in order to curb their cybercriminal business. Investigation into the activities of these groups has allowed Kaspersky Lab experts to form an idea about their methods of operation and the structure of the cybercriminal market.
Axarhöfði 14,
110 Reykjavik, Iceland














