eBay has no plans to fix severe bug
eBay has no plans to fix a "severe" vulnerability that allows attackers to use the company's trusted website to distribute malicious code and phishing pages, researchers from security firm Check Point Software said.
 The vulnerability allows attackers to bypass a key restriction that prevents user posts from hosting JavaScript code that gets executed on end-user devices.
The vulnerability allows attackers to bypass a key restriction that prevents user posts from hosting JavaScript code that gets executed on end-user devices.
eBay has long enforced the limitation to prevent scammers from creating auction pages that execute dangerous code or content when they're viewed by unsuspecting users. Using a highly specialized coding technique known as JSFUCK, hackers can work around this safeguard. The technique allows eBay users to insert JavaScript into their posts that will call a variety of different payloads that can be tailored to the specific browser and device of the visitor. "An attacker could target eBay users by sending them a legitimate page that contains malicious code," Check Point researcher Oded Vanunu wrote in a blog post published Tuesday.
"Customers can be tricked into opening the page, and the code will then be executed by the user's browser or mobile app, leading to multiple ominous scenarios that range from phishing to binary download." The post went on to say that Check Point researchers privately reported the security hole to eBay in mid-December. On January 16, eBay officials informed Check Point that they had no plans to issue a fix. The post didn't explain the reason behind eBay's decision.
In an e-mail sent to Ars after this post went live, eBay officials wrote: "eBay is committed to providing a safe and secure marketplace for our millions of customers around the world. We take reported security issues very seriously, and work quickly to evaluate them within the context of our entire security infrastructure. We have not found any fraudulent activity stemming from this incident.”
The e-mail added: Also, it's important to understand that we have been in touch with the researcher and have implemented various security filters based on his findings to detect this exploit. Since we allow active content on our site it's important to understand that malicious content on our marketplace is extraordinarily uncommon, which we estimate to be less than two listings per million that use active content on the eBay marketplace.
As the proof-of-concept exploit in the video above demonstrates, exploits require some element of social engineering, mostly in the form of a dialog box that instructs a user to OK the installation of a malicious app. Given the lack of security awareness of many of eBay's hundreds of millions of users and the site's walled-garden environment that aims to block malicious content, it's a fair bet that a significant number of people exposed to the threat would be tricked into infecting their devices or turning over their login credentials.
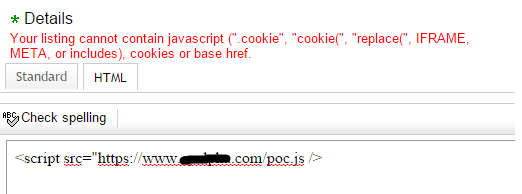
The vulnerability is the result of eBay's JavaScript filter failing to strip out characters that can be used to invoke executable code using the JSFUCK technique. Created by developer Martin Kleppe, JSFUCK is able to bypass a variety of intrusion prevention systems and Web application firewalls by using just different characters to execute code. As Check Point's Vanunu described:
To exploit this vulnerability, all an attacker needs to do is create an online eBay store. In his store details, he posts a maliciously crafted item description. eBay prevents users from including scripts or iFrames by filtering out those HTML tags. However, by using JSF**k, the attacker is able to create a code that will load an additional JS code from his server. This allows the attacker to insert a remote controllable JavaScript that he can adjust to, for example, create multiple payloads for a different user agent.
eBay performs simple verification but only strips alpha-numeric characters from inside the script tags. The JSF**k technique allows the attackers to get around this protection by using a very limited and reduced number of characters.
This is what you get if you include your remote website JavaScript:
This is how a simple JSF**k script looks:

This is how a successful exploitation of the vulnerability would look:
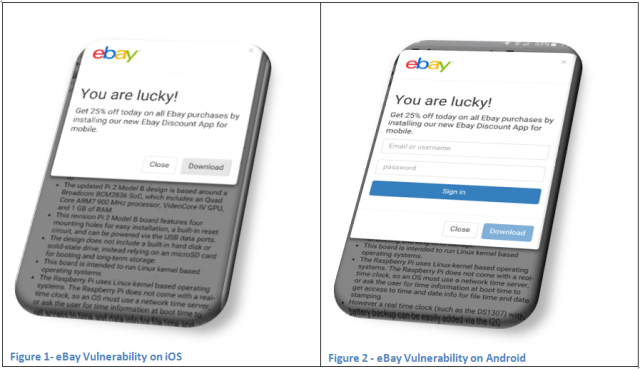
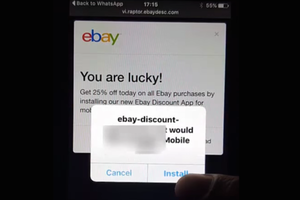
As shown, the message which appears on eBay’s website application (specifically, on the attacker’s store on the eBay site) entices the unsuspecting user into downloading a new eBay mobile application by offering a one-time discount.
For example, if a user taps the `download` button, he will unknowingly download a malicious application to his mobile device.
eBay's reported reluctance to patch the vulnerability is likely based on concerns that a fix will break current features or site functionality. Security has always been a series of trade-offs that balance convenience and productivity on the one hand and closing off feasible threats on the other. If the JavaScript bypass is as dangerous and easy to abuse as Check Point says, the degraded user experience may be worth it.
Axarhöfði 14,
110 Reykjavik, Iceland














