Attackers exploit Apple DRM weakness to infect non-jailbroken iOS devices
Palo Alto Networks revealed today the existence of a new iOS trojan called AceDeceiver that can infect both jailbroken and non-jailbroken devices, leveraging a design flaw in Apple's FairPlay DRM system.
 This design flaw is not new, it's called FairPlay Man-in-the-Middle, and was observed in the wild for the first time in February 2013, used for spreading pirated apps, and later presented in depth at the 23rd USENIX Security Symposium.
This design flaw is not new, it's called FairPlay Man-in-the-Middle, and was observed in the wild for the first time in February 2013, used for spreading pirated apps, and later presented in depth at the 23rd USENIX Security Symposium.
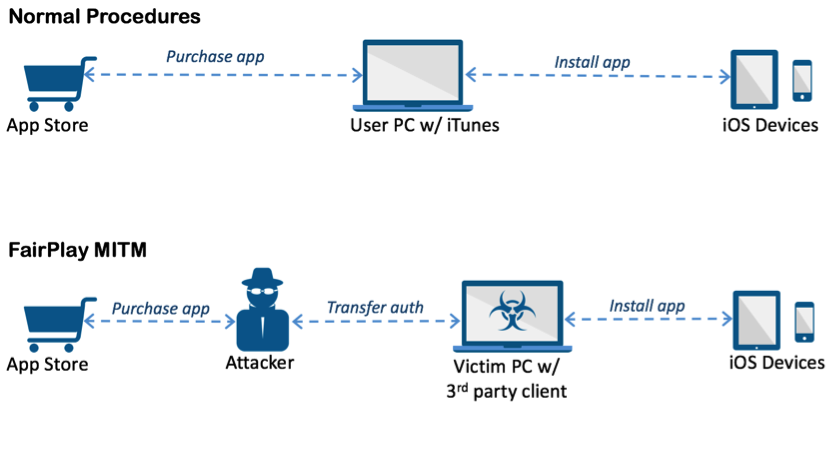
AceDeceiver marks the first time a FairPlay MitM attack was used to spread malware. FairPlay MitM is a simple MitM attack in which the attacker plays an intermediary role between the App Store and a user's computer or iOS device. When a user purchases an app from the App Store, they can optionally save it on their computer. When they want to install this app, the user, using iTunes installed on his computer, will request and receive an authorization code from Apple, to install the app on one of his devices.
A flaw in the FairPlay DRM allows the attacker to request this authorization code and then pass it to whatever device he chooses to (described in the picture below).
But more was needed to weaponize FairPlay MitMs, so attackers have then created a Windows software package called 爱思助手 (Aisi Helper), which to become appealing to users, also includes tools for jailbreaking devices, creating backups, and performing system cleaning operations.
This software also comes with a feature that allows users to install apps on their devices, some of which are offered from Apple's App Store, some of which from third-party stores.
Aisi Helper makes users think they've bought and paid for authentic apps from Apple's App Store when in fact the crook is recycling authorization codes while also abusing Aisi Helper to send malicious apps to the user's iOS device.
"Attackers tricked Apple into approving malicious apps on its official App Store"
Since FairPlay will block these apps from being installed on the device, the crooks also needed authorization codes from Apple's App Store for their malicious apps, infected with AceDeceiver. Using a bypass technique also employed by the ZergHelper family, AceDeceiver operators managed to upload three such apps on Apple's store.
Once on the official store, the crooks downloaded the apps on their devices, received the authorization code, and used these codes to forcibly push their malicious apps, infected with AceDeceiver, to any user that connected an iOS device to a PC running Aisi Helper. This installation process was hidden from view and continued to work after Apple detected the three AceDeceiver-infected apps and removed them from its store.
This happened because the authorization code remained valid, allowing the crooks to bypass the iOS device's FairPlay DRM system at later points, after Apple banned the original apps.
"Crooks only targeted Chinese users, this time"
As for AceDeceiver's capabilities, this trojan can steal Apple ID credentials, and will also act as a third-party store for installing other apps on infected devices for Chinese users. The way the AceDeceiver deceived Apple's code review process is simple. Because Apple provides App Stores for different regions of the globe, AceDeceiver's developers submitted the three malicious apps for listing on Apple's App Stores in areas outside China.
Since the trojan was not designed to exhibit any malicious behavior in those regions, Apple wasn't able to detect and flag their behavior at the time they were reviewed. Once they got Apple to approve the apps and issue authorization code, the crooks then used those codes to force Aisi Helper to install those apps behind the backs of Chinese users.
Currently, over 15 million Chinese users have downloaded Aisi Helper in the past two years. The three apps that crooks managed to pass by Apple's review process, infected with AceDeceiver, were simple wallpaper management applications.
"AceDeceiver is only targeting iOS devices in mainland China, but attackers could easily expand this attack to other regions around the world," Palo Alto Networks researchers explained. "And as we’ve already noted, the attack technique they’re exploiting will not be easy for Apple to fix." The name of the three AceDeceiver infected apps are aisi.aisiring, aswallpaper.mito, and i4.picture. Apple has removed them from its official store.

Axarhöfði 14,
110 Reykjavik, Iceland














