JavaScript-based malware attacks your router's DNS settings
Trend Micro researches discovered a new JavaScript-based malware that infects not only mobile devices but also attacks your home router, altering its DNS (Domain Name System) settings.
 Named JS_JITON, this new threat was first spotted in attacks at the end of December 2015, continuing to infect devices up until this day, hitting its peak in February 2016, with over 1,500 infections per day. The malware's infection chain is simple.
Named JS_JITON, this new threat was first spotted in attacks at the end of December 2015, continuing to infect devices up until this day, hitting its peak in February 2016, with over 1,500 infections per day. The malware's infection chain is simple.
According to Trend Micro researchers, attackers place malicious code on compromised websites and wait for users to visit these pages using mobile devices. Once this happens, the malware is downloaded to the user's mobile device and executes, trying to connect to the local home network's router IP using a series of admin and passwords combos hardcoded in the JS_JITON malware source code. Over 1,400 credentials are included, and once the malware authenticates on the device, it will change the router's DNS settings.
JS_JITON is still a work in progress, evolves each week
It is unknown why the malware executes this routine, but taking into account that at one point it also included malicious code that executed from desktop computers, Trend Micro researchers believe this is a "work in progress," with its creators still exploring their attack's capabilities.
This conclusion is also reinforced by the fact that attackers regularly update JS_JITON's source code, changing small details here and there, fine tuning their attacks. Additionally, at one point, the JS_JITON source code also included a keylogging component. Researchers noted that JS_JITON could attack D-Link and TP-Link routers, but it also included a special exploit to take advantage of CVE-2014-2321, an older vulnerability in ZTE modems.
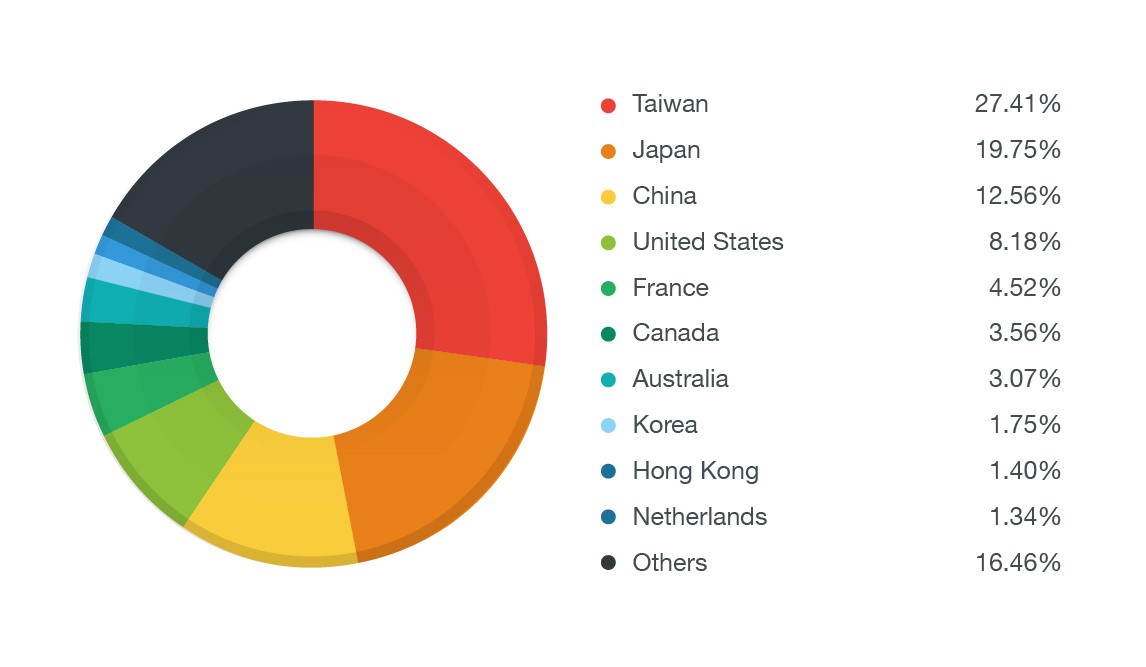
Most of the malicious JS_JITON code is hosted on infected sites in Russia and Asian countries, but this hasn't stopped attackers from making victims all over the world. Most infected devices are found in Taiwan (27%), Japan (20%), China (13%), the US (8%), and France (5%).
Axarhöfði 14,
110 Reykjavik, Iceland














