QRLJacking — hacking technique to hijack QR code based quick login system
Do you know that you can access your WeChat, Line and WhatsApp chats on your desktop as well using an entirely different, but fastest authentication system?
 It's SQRL, or Secure Quick Response Login, a QR-code-based authentication system that allows users to quickly sign into a website without having to memorize or type in any username or password.
It's SQRL, or Secure Quick Response Login, a QR-code-based authentication system that allows users to quickly sign into a website without having to memorize or type in any username or password.
QR codes are two-dimensional barcodes that contain a significant amount of information such as a shared key or session cookie. A website that implements QR-code-based authentication system would display a QR code on a computer screen and anyone who wants to log-in would scan that code with a mobile phone app. Once scanned, the site would log the user in without typing in any username or password. Since passwords can be stolen using a keylogger, a man-in-the-middle (MitM) attack, or even brute force attack, QR codes have been considered secure as it randomly generates a secret code, which is never revealed to anybody else. But, no technology is immune to being hacked when hackers are motivated.
QRLJacking: Hijacking QR Code Based Login System
Egyptian Information security researcher and Cyber Security Advisor at Seekurity Inc. Mohamed Abdelbasset Elnouby has come up with a proof-of-concept demonstrating a new session hijacking technique that can be used to hack accounts from services that use "Login with QR code" feature as a secure way to login to accounts. Dubbed QRLJacking (or Quick Response code Login Jacking), the technique is a "simple-but-nasty attack vector" that affects all the applications that rely on Login with QR code feature. All an attacker needs to do is to convince the victim into scanning the attacker's QR code.
Here's How QRLJacking Technique Works:
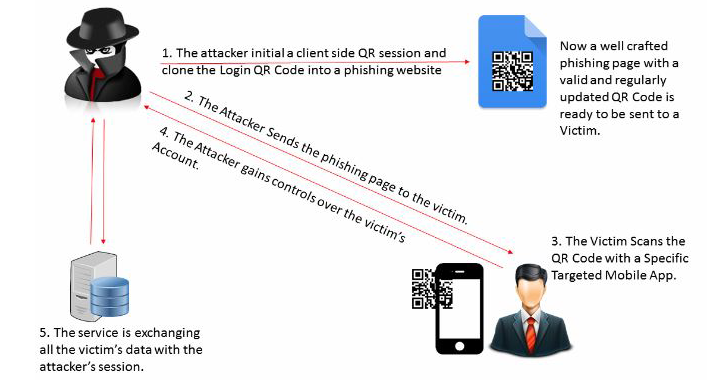
Mohamed explained me the complete working of QRLJacking attack, along with live demonstration, via Skype. Here's how the attack works:
- The attacker initializes a client side QR session and clones the Login QR Code into a phishing page.
- The attacker then sends the phishing page to the victim.
- If convinced, the victim scans the QR Code with a specific targeted Mobile App.
- The mobile app sends the secret token to the target service to complete the authentication process.
- As a result, attacker, who initializes a client side QR session, gains control over the victim's account.
- Then the service starts exchanging all the victim's data with the attacker's browser session.
So, to carry out a successful QRLJacking attack, all an attacker needs:
- A QR Code Refreshing Script.
- A well crafted Phishing Web page.
Video Demonstration: Hacking Whatsapp Account Using QRLJacking
"The attackers need to do to initialize a successful QRLJacking attack is to write a script to regularly clone the expirable QR Codes and refresh the ones displayed on the phishing website which they created, because as we know a well implemented QR Login process should have an expiration interval for the QR codes," the explanation reads.
A successful QRLJacking attack gives an attacker the ability to apply a full account hijacking scenario on the vulnerable QR-Code-based Login service resulting in account hijacking and other information like victim's accurate current GPS location, device IMEI number, SIM card data and other sensitive data that the client app presents at the login process.
Axarhöfði 14,
110 Reykjavik, Iceland














