Wi-Fi signal interference can leak your passwords and keystrokes
Hackers can steal your sensitive information, such as your Passwords, PINs and Keystrokes, from your phone by observing changes in the wireless signal as you enter them into your smartphones.
 A group of researchers from the Shanghai Jaio Tong University, the University of South Florida and the University of Massachusetts at Boston have demonstrated a new technique that can reveal private information by analyzing the radio signal Interference, using just one rogue Wi-Fi hotspot.
A group of researchers from the Shanghai Jaio Tong University, the University of South Florida and the University of Massachusetts at Boston have demonstrated a new technique that can reveal private information by analyzing the radio signal Interference, using just one rogue Wi-Fi hotspot.
Dubbed WindTalker, the attack sniffs a user's fingers movement on the phone's touchscreen or a computer's keyboard by reading the radio signal patterns called Channel State Information (CSI). CSI is part of the Wi-Fi protocol which provides general information about the status of the Wi-Fi signal. "WindTalker is motivated from the observation that keystrokes on mobile devices will lead to different hand coverage and the finger motions, which will introduce a unique interference to the multi-path signals and can be reflected by the channel state information (CSI)," the researchers writes in their paper titled, 'When CSI Meets Public Wi-Fi: Inferring Your Mobile Phone Password via Wi-Fi Signals.'
"The adversary can exploit the strong correlation between the CSI fluctuation and the keystrokes to infer the user’s number input." Here’s How An Attacker Track your fingers moves on a smartphone screen:
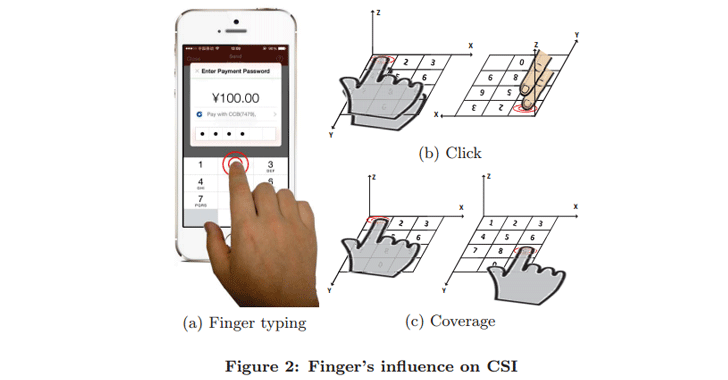
When you enter your PIN number or password in any app or swipe your smartphone lock screen pattern, your finger movements alter the Wi-Fi signals transmitted by a mobile phone, and the movements are imprinted into the signal.
Now, hackers with control to a public Wi-Fi hotspot to which your device is connected to could then intercept, analyze, and reverse engineer those signals to accurately guess what sensitive data you have typed into your phone or in password input fields.
The WindTalker attack is particularly effective as it does not require any access to the victim's phone and works with regular mobile phones.
The attack needs the hacker to control a rogue Wi-Fi access point to which the target will connect to and collect Wi-Fi signal disturbances.
WindTalker will also not work with older internet router that has one antenna to broadcast Wi-Fi signals around your home, as it relies on a technology called Multiple Input, Multiple Output (MIMO).
However, this is not a problem because the latest wireless routers now come with multiple antennas and MIMO technology, which enables routers to connect and transmit data from multiple devices simultaneously.
WindTalker Attack has an Over 68% Accuracy
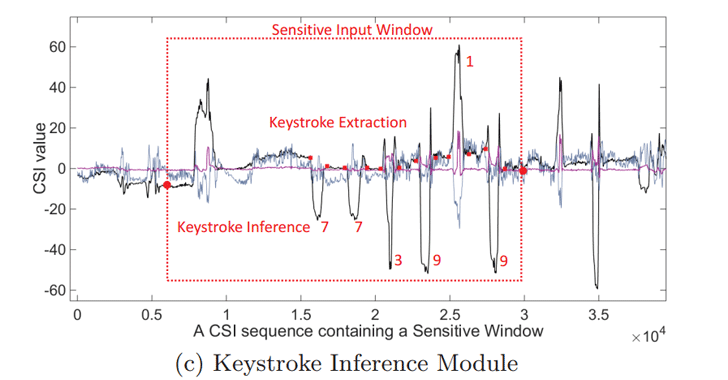
The researchers tested the WindTalker attack in a real-world scenario against several mobile phones and were able to recover the 6-digit transaction PIN required to complete a mobile payment transaction via Chinese Payment Service Alipay.
The accuracy of the WindTalker attack is different based on mobile phone models, and the accuracy could also be improved with users typing more and the attacker collecting more data on it. The WindTalker attack technique was also presented at the 23rd Association for Computing Machinery Conference on Computer and Communications Security, held in Vienna, Austria, from 24 to 28 October.
Axarhöfði 14,
110 Reykjavik, Iceland














