Hackers can now use sound waves to take control of your smartphone
There’s an old mantra in the security world that anything can be hacked. And the more complex our devices become, the more methods hackers dream up to break into them.
 Case in point: A team of researchers can use sound waves to control anything from a smartphone (seriously) to a car (theoretically). The trick boils down to spoofing capacitive MEMS accelerometers, the chips that enable smartphones and Fitbits to know when they’re in motion, where they’re going, and how quickly.
Case in point: A team of researchers can use sound waves to control anything from a smartphone (seriously) to a car (theoretically). The trick boils down to spoofing capacitive MEMS accelerometers, the chips that enable smartphones and Fitbits to know when they’re in motion, where they’re going, and how quickly.
Using a small $5 speaker, researchers at the University of Michigan and the University of South Carolina blasted 20 different accelerometers from five manufacturers with sound waves from malicious music files. The resonant frequencies tricked the sensors in more than half of the accelerometers tested, enabling the researchers to do all sorts of stuff. “It’s like the opera singer who hits the note to break a wine glass, only in our case, we can spell out words [and send commands to a smartphone]” Kevin Fu, an associate professor of electrical engineering and computer science at Michigan told. “You can think of it as a musical virus.”
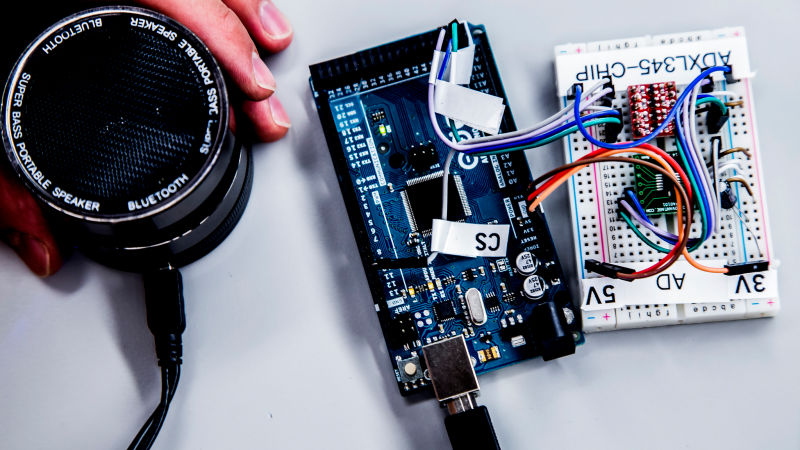
The sonic cyber attack actually works almost exactly how you’d think it would. Capacitive MEMS accelerometers contain a small amount of mass suspended on springs, and the sound waves nudge that piece of mass in such a way that the chip thinks it’s in motion. The team explains exactly how the method works on a new website about the project.
The possibilities of this simple attack are nothing short of unnerving. Fu and his team used these sonic cyber attacks to trick smartphones into executing whatever command they wanted. The researchers show in a video how they can take over a smartphone app that controls a toy car using nothing but sound waves. They also spoofed a Fitbit into counting steps while the device remained perfectly still. The team gained so much control over the accelerometers that they could force a Samsung Galaxy S5 to spell out words in the chip’s output signal.
But that’s only the beginning. With the right knowledge of how certain apps work, a malicious hacker could potentially take over a smartphone app with the right combination of sound waves. “If a phone app used the accelerometer to start your car when you physically shake your phone, then you could intentionally spoof the accelerometer’s output data to make the phone app think the phone is being shaken,” Timothy Trippel, the lead author of a new paper on the WALNUT project and a PhD candidate at Michigan, told Gizmodo. “The phone app would then send the car a signal to start.”
Along these lines, it’s important to highlight that these experiments were proof-of-concept exercises that exposed serious vulnerabilities in popular consumer hardware. Pwning a smartphone to drive a toy car isn’t particularly dangerous, but the same kinds of accelerometer technology is used in real cars, drones, airplanes, medical devices, and other connected devices.
Experts hinted at “darker possibilities” for a cyber attack like this, giving the example of how accelerometers in insulin pumps could be tricked into giving the wrong dosage. Just imagine the apocalyptic possibility of broadcasting a malicious music file over the radio that makes certain cars crash into each other on the highway. This is scary stuff.
“Thousands of everyday devices already contain tiny MEMS accelerometers,” Fu said in a release. “Tomorrow’s devices will aggressively rely on sensors to make automated decisions with kinetic consequences.” The researchers have shared their findings with the manufacturers of the vulnerable accelerometers. And accordingly, on Tuesday, the Department of Homeland Security issued an alert about the hardware design flaws, detailing which chips were at risk and what can be done to mitigate the risk of a real-world attack. So if you ever questioned whether or not we’re living in a very long, anxiety-ridden episode of Black Mirror, wonder no more. We are, and it’s nuts.
Axarhöfði 14,
110 Reykjavik, Iceland














