About 90% of smart TVs vulnerable to remote hacking via rogue TV signals
A new attack on smart TVs allows a malicious actor to take over devices using rogue DVB-T (Digital Video Broadcasting — Terrestrial) signals, get root access on the smart TV, and use the device for all sorts of nasty actions, ranging from DDoS attacks to spying on end users.
 The attack, developed by Rafael Scheel, a security researcher working for Swiss cyber security consulting company Oneconsult, is unique and much more dangerous than previous smart TV hacks.
The attack, developed by Rafael Scheel, a security researcher working for Swiss cyber security consulting company Oneconsult, is unique and much more dangerous than previous smart TV hacks.
Until now, all smart TV exploits relied on attackers having physical access to the device, in order to plug in an USB that executes malicious code. Other attacks relied on social engineering, meaning attackers had to trick users into installing a malicious app on their TV. Even the mighty CIA developed a hacking tool named "Weeping Angel," which could take over Samsung smart TVs and turn them into spying devices. But despite its considerable human and financial resources, the CIA and its operators needed physical access to install Weeping Angel, which made it less likely to be used in mass attacks, and was only feasible if deployed on one target at a time, during carefully-planned operations.
Because of the many constraints that come with physical and social engineering attacks, Scheel didn't consider any of them as truly dangerous, and decided to create his own.
Scheel's attack is remote, no user interaction needed
Scheel's method, which he recently presented at a security conference, is different because the attacker can execute it from a remote location, without user interaction, and runs in the TV's background processes, meaning users won't notice when an attacker compromises their TVs.
The researcher told via email that he developed this technique without knowing about the CIA's Weeping Angel toolkit, which makes his work even more impressing. Furthermore, Scheel says that "about 90% of the TVs sold in the last years are potential victims of similar attacks," highlighting a major flaw in the infrastructure surrounding smart TVs all over the globe.
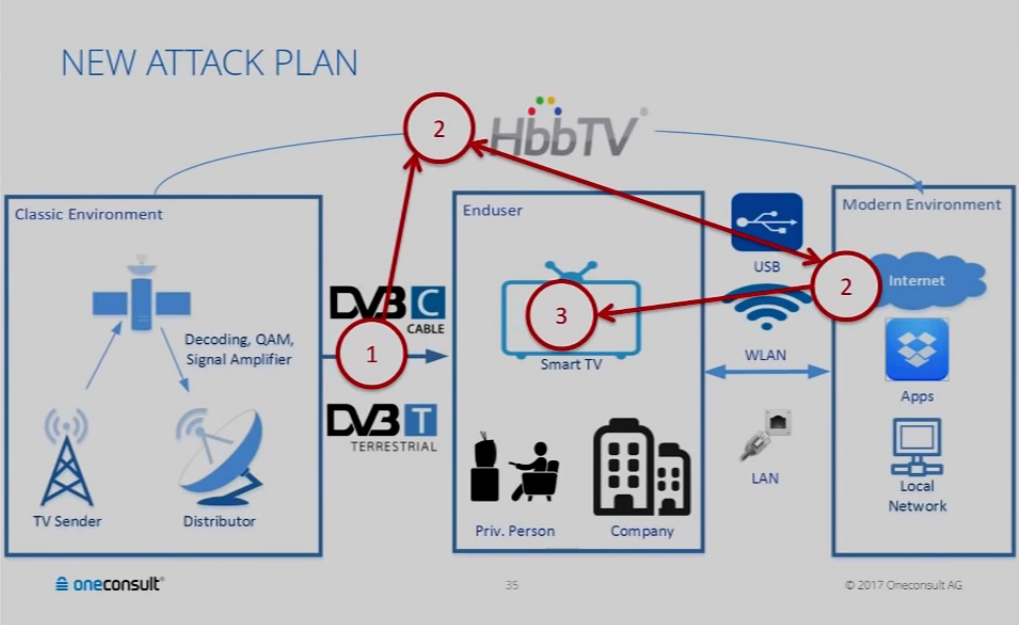
At the center of Scheel's attack is Hybrid Broadcast Broadband TV (HbbTV), an industry standard supported by most cable providers and smart TV makers that "harmonizes" classic broadcast, IPTV, and broadband delivery systems. TV transmission signal technologies like DVB-T, DVB-C, or IPTV all support HbbTV. Scheel says that anyone can set up a custom DVB-T transmitter with equipment priced between $50-$150, and start broadcasting a DVB-T signal.
Rogue TV signals could deliver malicious HbbTV commands
By design, any nearby TV will connect to the stronger signal. Since cable providers send their signals from tens or hundreds of miles away, attacks using rogue DVB-T signals could be mounted on nearby houses, a neighborhood, or small city. Furthermore, an attack could be carried out by mounting the DVB-T transmitter on a drone, targeting a specific room in a building, or flying over an entire city.
According to Scheel, the problem is that the HbbTV standard, carried by DVB-T signals and supported by all smart TVS, allows the sending of commands that tell smart TVs to access and load a website in the background. Knowing this, Scheel developed two exploits he hosted on his own website, which when loaded in the TV's built-in browser would execute malicious code, gain root access, and effectively take over the device.
For his first exploit, Scheel used CVE-2015-3090, which is one of the Flash zero-days leaked in the Hacking Team 2015 incident. After coding and successfully testing the exploit, Scheel realized that not all smart TV browsers come with the Flash Player plugin enabled by default.
Because of this, Scheel developed a second exploit, which exploited an older vulnerability in the Array.prototype.sort() JavaScript function, support by all browsers, even by those shipped with smart TVs. This second exploit allowed him to escalate access from the user's browser to the underlying smart TV firmware, doing the same thing as the first (Flash) attack, but without relying on the presence of the Flash plugin.
Attack is almost untraceable
Scheel says his attack benefits from the way the smart TV ecosystem has developed. The researcher is referring to the fact that there are much fewer smart TV models on the market and a much higher homogeneity between their operating systems, than compared with personal computers, meaning an attacker could target a wide range of TVs without having to create different versions of his exploit.
Furthermore, because delivering smart TV firmware updates isn't a streamlined process, security flaws remain in the wild for years, or in some cases, forever, despite the fact that TV vendors fixed issues many years before. But the best feature of his attack, which makes his discovery extremely dangerous, is the fact that DVB-T, the transmission method for HbbTV commands, is a uni-directional signal, meaning data flows from the attacker to the victim only.
This makes the attack traceable only if the attacker is caught transmitting the rogue HbbTV signal in real-time. According to Scheel, an attacker can activate his HbbTV transmitter for one minute, deliver the exploit, and then shut it off for good. Forensics experts investigating the hack would have no way of tracing back the attack to its source over DVB-T unless the attacker started broadcasting again.
It's almost impossible to clean infected smart TVs
Because the attack takes minutes to execute and the user doesn't notice anything, Scheel's discovery is a technique that's tailor-made for nation-state surveillance operations. The recent WikiLeaks revealed an active interest in hacking embedded (IoT) devices on the CIA's part.
In addition, any backdoors added through this method are almost impossible to remove, as the attacker could sabotage any firmware update mechanism and remain on the device until users got rid of their smart TVs. Furthermore, Scheel says factory reset operations didn't help for the devices he tested, and the backdoor he developed remained on the TVs.
The researcher says that such a backdoor could be used to run IoT DDoS botnets, use the smart TVs as relay points for attacks on enterprise networks, spy on users via the TV's microphone and camera, steal data stored on the TV, inject ads on the TV (sabotage competitors on the smart TV market), and many other actions.
In his presentation, Scheel says that he doesn’t understand the HbbTV security concept. "For me, it's really dangerous to use such an untrusted signal to do something really critical," the researcher said. "In website security, calling a different website would be classified as a vulnerability." But apparently not in smart TVs.
Attacks via DVB-C and IPTV are also possible
Scheel says he tested his attack with rogue HbbTV commands via DVB-T signals only, but, in theory, the attack should also work over DVB-C (Digital Video Broadcasting - Cable) and IPTV channels as well. The problem of sending rogue HbbTV commands is not anything new. According to Scheel, researchers from Columbia University spotted this issue in 2015, but they were largely ignored by the HbbTV Consortium because they did not include an exploit that hacked the smart TV, which would have guaranteed an adequate response.
The researcher has presented his attack at the EBU (European Broadcasting Union) Media Cyber Security Seminar held in Geneva, Switzerland, last month. A video of his presentation, which also includes demonstrations for both DVB-T attacks and proposed mitigations, is embedded below.
Axarhöfði 14,
110 Reykjavik, Iceland














