Password Reset MITM: Exposing the need for better security choices
Attackers that have set up a malicious site can use users’ account registration process to successfully perform a password reset process on a number of popular websites and messaging mobile applications, researchers have demonstrated.
 The Password Reset Man in the Middle (PRMITM) attack exploits the similarity of the registration and password reset processes.
The Password Reset Man in the Middle (PRMITM) attack exploits the similarity of the registration and password reset processes.
To launch such an attack, the attacker only needs to control a website. To entice victims to make an account on the malicious website, the attacker can offer free access to a wanted resource (e.g. free software). Once the user initiates the account registration process by entering their email address, the attacker can use that information to initiate a password reset process on another website that uses that piece of information as the username (e.g. Google, YouTube, Amazon, Twitter, LinkedIn, PayPal, and so on).
Every request for input from that site is forwarded to the potential victim, and then his or her answers forwarded back to that particular site. In the most basic form (when the password reset request depends on security questions), the attack looks like this:
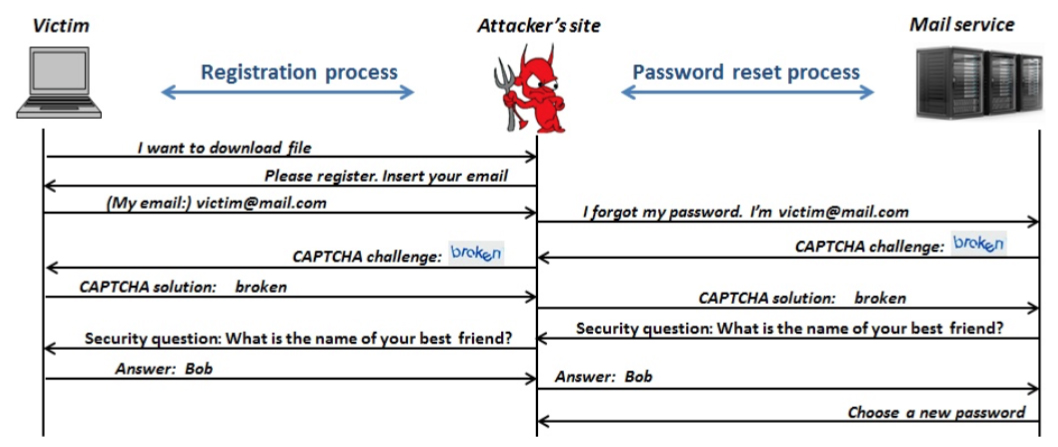
But the attack is also very successful if the password reset request depends on an SMS code for confirmation, or a phone code delivering the code. The potential victim is, along with the email address, asked to input their mobile phone number so that the malicious site can “verify” that they are who they say they are and, in the majority of cases, they fail to find it suspicious that the SMS or phone call is coming from Google, or Facebook, and so on.
That failure is down to several things:
- Some sites fail to identify themselves as the sender of the SMS or the caller delivering the code (e.g. the user sees just a phone number, and the message does not explicitly say from which service it comes from)
- Many users don’t read or really hear the text in the message/phone call – they simply do not register it – but zero-in on the offered numeric code. Some users do not even open the message, but read the code from the notifications bar
- A reset code message may come in an unknown language, confusing users and making them focus even more on just the code
- Some users may notice that the message was sent from Facebook (for example), but perhaps believe that the login is done using the widely used login with Facebook mechanism.
Workable solutions
The researchers have executed a few experiments, confirming the high probability of such an attack to be successful, and have notified of their findings the companies running many popular websites that have vulnerable password reset processes.
They have shared with them some general guidelines that can be applied to prevent Password Reset MITM attacks, including avoiding relying on security questions, restricting the validity of the reset code to a short time, notifying users by email and phone when a password reset request is sent, not sending a code but a link, and adding interactivity to the phone call so that users are forced to listen to the message and understand what they are doing.
“Vendors that are severely vulnerable to the PRMITM attack, either fixed the vulnerability (Snapchat, Yahoo!) or informed us that they plan to fix the vulnerability (Google, LinkedIn and Yandex). Other websites, which are less vulnerable (e.g., Facebook) thanked us, and told us they will consider using our findings in the future, but they do not plan to apply fixes soon,” the researchers concluded.
Download SafeUM — communicate privately, without advertising and spam.
Axarhöfði 14,
110 Reykjavik, Iceland

















