One-day wonders: here today, gone tomorrow
Websites come and go over time; rarely is a second thought given to those sites left by the wayside.
 Recently, the Blue Coat Security Labs team has looked into the nature of the host names that make up the Web, and the fleeting nature of many of them is truly surprising.
Recently, the Blue Coat Security Labs team has looked into the nature of the host names that make up the Web, and the fleeting nature of many of them is truly surprising.
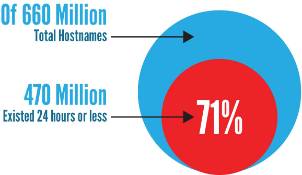
In a recent 90-day period of traffic, we counted over 660 million unique host names. (That’s about one host name for every 10.6 people in the world.) While the sheer number of hosts is notable, more remarkable is the volume of hosts that were present for only a single day in that 90-day window; we call these hosts “one-day wonders”.
An astounding 71% (~470M) of the hosts were so transient that they only appeared in a single day's traffic over the course of 12 weeks. Despite the famed speed at which new sites and services come online, and the Internet’s highly distributed nature, this percentage seemed a bit extreme -- what was going on in there?
 It is not intuitive that something would exist so briefly. The skeptical mind promptly questions whether these sites exist at all. Are these simply vacuous requests to misspelled or unallocated host names? The paranoid part of the brain suggests that these must be randomly generated domain names used to control the millions of infected machines throughout the world. Digging deeper into the data provided some answers.
It is not intuitive that something would exist so briefly. The skeptical mind promptly questions whether these sites exist at all. Are these simply vacuous requests to misspelled or unallocated host names? The paranoid part of the brain suggests that these must be randomly generated domain names used to control the millions of infected machines throughout the world. Digging deeper into the data provided some answers.
Identifying the Big Players
Host names can be numeric IP addresses or textual domain (or subdomain) names. Of the one-day wonders, ~164M used IP addresses as their host names (1.8M per day, on average). That’s roughly 5% of the publicly routed IPv4 address space that appeared only for one day in a three month period in normal Web traffic. Looking at the autonomous systems (AS) that own these IP addresses, ISPs and Telcos clearly dominated the top 10, but their individual percentages were so low that there really was no one entity that stood above the rest.
With almost double the amount(~305M) of one-day wonder IP addresses, domain and subdomain names were where most of the action was. The near exhaustion of the IPv4 space is definitely a contributing factor, but the simplicity of adding a DNS entry is perhaps the foremost contributing factor. It also helps that the number of theoretically possible domain names dwarfs even the vast quantity of IPv6 addresses.
Examining the top-level domain (TLD) of these hosts began to shed some light on where this behavior is rooted. The TLD .com dwarfed every other TLD; it was 2.5 times greater than all other TLDs combined. Other TLDs like .net and .info merit mention, but, clearly, ephemeral domains prefer the .com neighborhood above any other. Drilling down one more step in the DNS hierarchy revealed the big players.
Google is clearly the king when it comes to the use of short-lived subdomains, with nearly half of the total count. Content Delivery Networks (CDNs) are also highly ranked (including a porn site at #7). While it was evident that a majority of short-lived names appeared to serve a legitimate purpose, we didn't need to look very far to find the malicious content.
Evil takes Evasive Action
We have long observed that Malnet operators love to generate large numbers of evil domains. These transient sites are a critical component of mass attack support infrastructures. They ensure additional bots can easily be added to an existing army and give cyber criminals the ability to manage their botnets for a longer period of time, increasing the return on investment for any given attack.
For example, One-day Wonders can be used to build dynamic Command-and-Control architectures that are scalable, difficult to track and easy to implement. Alternatively, they can be used to create a unique subdomain for each spam email to throw off spam or web filters.
One-day Wonders are particularly popular with cybercriminals because they:
Keep security solutions guessing
Overwhelm security solutions
Hide from security solutions
Looking back through the top 50 parent domains, just two spots removed from the top 10 parent domains.
This perplexing parent domain is a C&C server for a botnet. Over the 90-day period it had over 1.3M unique subdomains. And it was not alone. There were ten more similar parent domains that served as C&C infrastructure that showed up in the top 50 list. This family of sites, by itself, provided 20%+ of the membership in the top 50. The bad guys are clearly quite active in this space.
Axarhöfði 14,
110 Reykjavik, Iceland














