Look for the weaknesses of modern password managers
Despite the fact that a lot of ways of authentication and access control were invented in the world, only password is the most common and the most vulnerable as well. Many internet portals and services forbid users to create simple passwords for their safety.
 On the one hand it a good idea, but on the other hand it is uncomfortable. If we multiply this fact to a dozen of such sites, we will have a real headache.
On the one hand it a good idea, but on the other hand it is uncomfortable. If we multiply this fact to a dozen of such sites, we will have a real headache.
To eliminate the problem between the human factor and data security the aid of password managers is needed, they take on the organization of users' passwords. However, it turns out that the safety of the user depends on a Master Password only.
WARNING
All information is provided for informational purposes only. Neither the editors, nor the author will be responsible for any possible damage, caused by the materials in this article.
The formulation of the problem
The well-known password managers have been compared for many times before, but today we are going to talk about their security in general. In this article, we discuss the protection of password managers critically and consider several options for the attack on the popular managers in order to obtain a master password or the ability to obtain data partially, stored in the password database.
As examinees five of the most popular solutions were chosen for Microsoft Windows:
- Kaspersky Password Manager 5.0.0.176;
- Sticky Password 7.0.2.27;
- 1Password 1.0.9.337;
- KeePass 2.23;
- RoboForm 7.9.2.5
Each of them will be checked on the vulnerability of the following attacks:
- attack on a Master Password;
- attack on the contents of the password database;
- DLL Hijacking attack.
According to the results we will put each of them corresponding mark: bad, satisfactorily or good.
Attack on passwords
As you know, password managers do not save a Master Password anywhere on your computer, and every time the user has to enter it by hand while using manager. However, in our case, we will not write complex shadow drivers to intercept keystrokes and screen shots, as they can put our attack in laboratory conditions and can be detected by antivirus easily.
We examine a very interesting, but not a new method of obtaining the password directly from the input window by calling the API SendMessage with WM_GETTEXT parameter. This method is remarkable, because many antivirus software programs will not recognize it as a potentially dangerous operation, and will be realized by pairs of code lines, plus administrator rights are not required to run it.
Moreover the attack through SendMessage can be used to receive text data from any application windows, so even if a Master Password doesn’t yield, there will be a high probability of partial or complete obtaining the contents of the database itself after its opening.
DLL Hijacking
In addition, we are going to check the vulnerability of each manager to DLL Hijacking attack to see how well each of them loads the dynamic libraries. If the possibility to substitute the loading library by your own is found, then we will be able to execute arbitrary code on the system. And although this attack is a subject to a large number of different applications, in the case of password managers, it has its own nuance.
Many users often work on different computers, so they are launching password managers from removable storage devices. While such launchings for many times the unauthorized library is loaded, in fact password manager turns into a dangerous distributor of viruses.
Write SendMessage-exploit
It is not effective to write its own exploit for each password manager, so it‘s better to write a universal one. The advantages of such an exploit are that with its help we may not only "pull" a Master Password and saved passwords in the database, but also use it for other applications, which have a form of the password. In fact, we will get a simple and convenient hacktool that can obtain passwords, quickly answer the question for any application. Well, now here's the coding.
At first we need a function that will prepare a memo field for a new data adoption and determine the handle of the main window under the cursor, and then it will receive "daughter" windows handles and pass the subsequent functions to recognize the contents of the window.
EnmWndwsWnd function will be responsible for "daughter" windows content output.
After starting, the program using the timer will track the cursor position on the screen and define the text below it, so it is enough to put the cursor on the necessary field to find out the password instantly. Furthermore, with the help of this tool the textual content of all windows in the application can found. This function is useful to scan the contents of the password database quickly after opening the manager.
Look for DLL Hijacking vulnerabilities
The well-known Procmon can be used in order to detect DLL Hijacking. Apart from Procmon, another popular API Monitor utility may be used, where you must first specify the interception of LoadLibrary and LoadLibraryEx functions in the relevant settings menu. If the library was called without specifying the full path, but a final name of the file was pointed out, then we have all chances to find a vulnerable DLL-file. Now let‘s write a small code that can signal on vulnerability and as an evidence open the calculator.
The created library will open calculator every time when the application launches it, so we may say that it is DLL Hijacking.
INFO
All described vulnerabilities in Kaspersky Password Manager and Sticky Password existed three years ago. Despite the fact that vendors were warned, as you can see, the problem still remains.
Kaspersky Password Manager 5.0.0.176
Now it's time to judge the password managers‘ safety. The first examinee is Kaspersky Password Manager. Perhaps the virtual keyboard could help him in the case of keyloggers, but in our case the a Master Password was obtained immediately, without any difficulties. The first round is not in favor of "Kaspersky Lab".
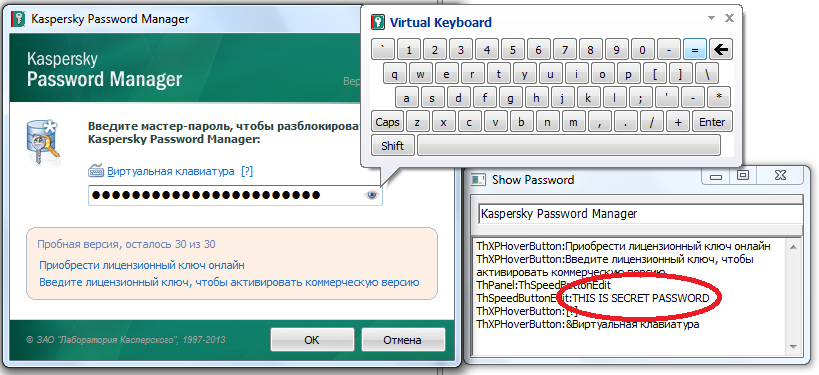
Our hack-tool also won the second round. After entering the master password the stored data was partially got at the time of viewing or editing.
In addition, KMP was attacked by DLL Hijacking. At the start it tries to load the bthprops.cpl library. The library is in the system folder and is required to work with Bluetooth-enabled devices, but KMP tries to run it, without specifying the full path, it was the reason for the vulnerability. The situation with another library cryptsp.dll loading is the same. It is enough to place a malicious library, which, for example, may contain an exploit for the previous two attacks in the same folder as the application and rename it bthprops.cpl, after which it will be loaded each time you start the KMP.
To summarize, we can say that Kaspersky Password Manager didn’t impress. The final mark is bad.
Sticky Password 7.0.2.27
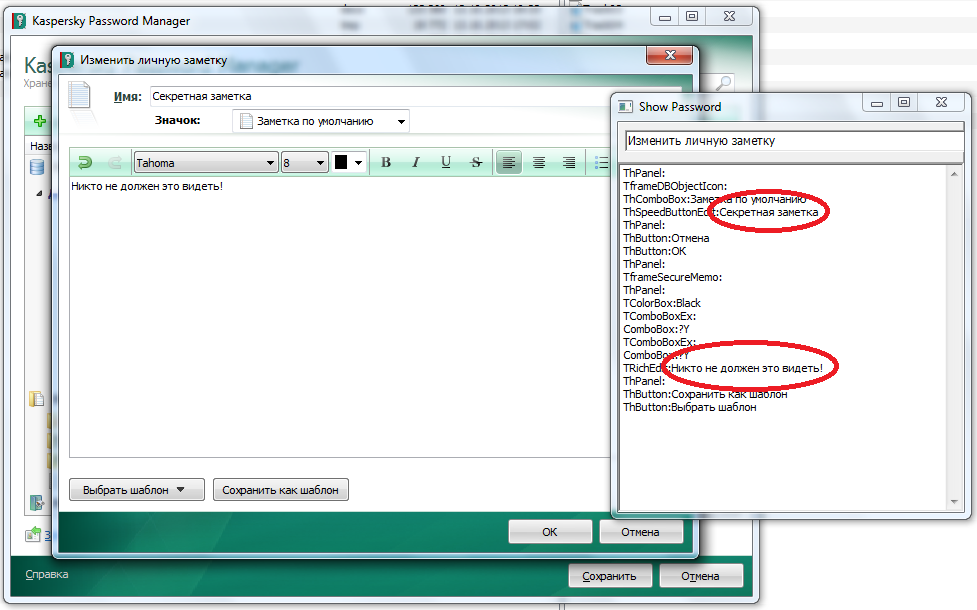
A few people know that Kaspersky Password Manager developed its own product, which was based on Sticky Password. Both managers have similar functionality and structure; in fact the main difference between them is the version number and design. Despite the latest version of Sticky Password have been released recently, the program still didn’t get rid of all the problems. The first and second attacks successfully issued a Master Password and partially the contents of the password database.
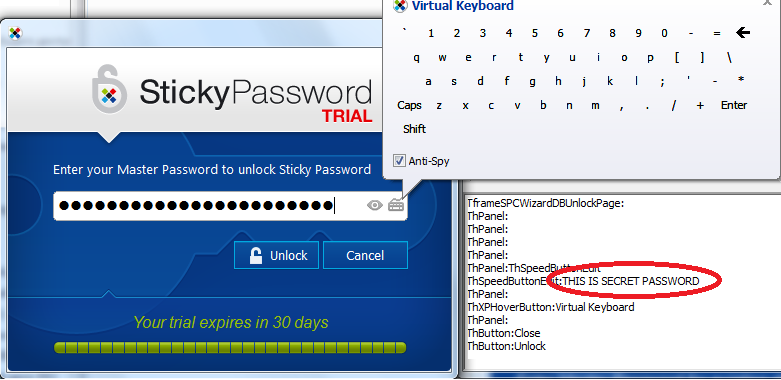
As Kaspersky Password Manager, Sticky Password didn’t win a third round: a number of DLL Hijacking vulnerabilities were identified. When starting, the application tries loading some dynamic libraries from its own folfer: fitlib.dll, olepro32.dll, profapi.dll. The overall verdict is the same as in the Kaspersky Password Manager. The final mark is bad.
1Password 1.0.9.337
1Password from Agile Bits Company was successful and a Master Password wasn’t obtained easily as in two examples above. Also the existence of protective Unlock on Secure Desktop function pleased, it blocks any access to the application when a password is entering. The only moment when our attack could obtain a Master Password was the time of creating a password database. However, this method is rarely used in practice, so we do not consider its results. After opening the database to get stored data was possible partially when editing or viewing, as in the previous cases.
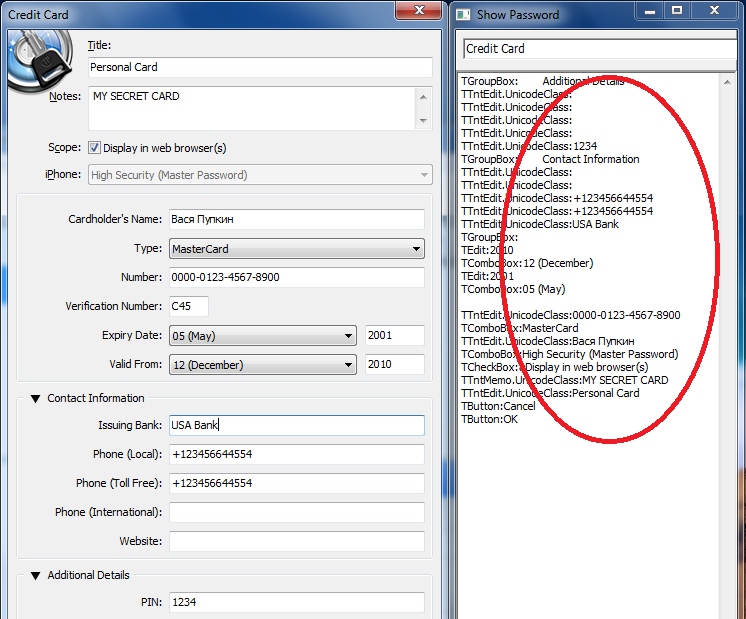
DLL Hijacking touched 1Password as well. After opening the database, application tries loading a midimap.dll library. Despite a number of vulnerabilities, the presence of the protective password function is inclined to the neutral point of view; therefore, the final mark is satisfactory.
KeePass 2.23
The well-known KeePass managed with the first attack. Like 1Password, it has at an access control function to the application while entering a password. The second attack was prevented by KeePass . The recorded data in the base may be obtained while editing only, and the saved passwords remain unexposed. The third attack is also in favor of an open source password manager.
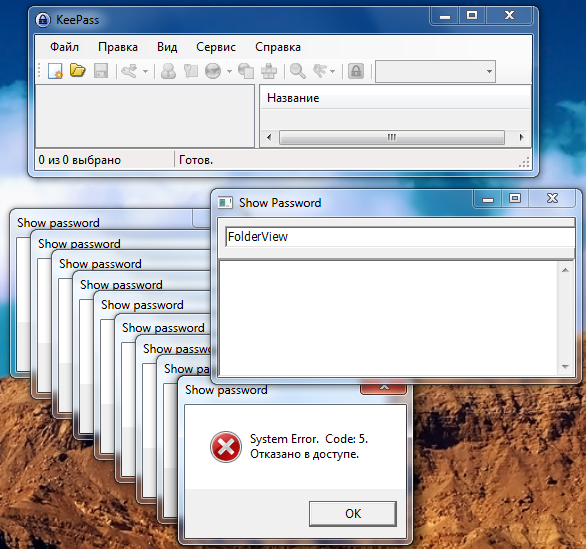
Although Procmon showed several attempts to download unsafe DLL-files, still it was impossible to make the working exploit on their base. Credit is in favor of GNU-community. The final mark is good.
RoboForm 7.9.2.5
RoboForm doesn’t give up at the first attack and it did not give its Master Password, for which it received plus. However, the second round was not in his favor. Even in playback mode almost the entire contents of the forms was easily obtained.
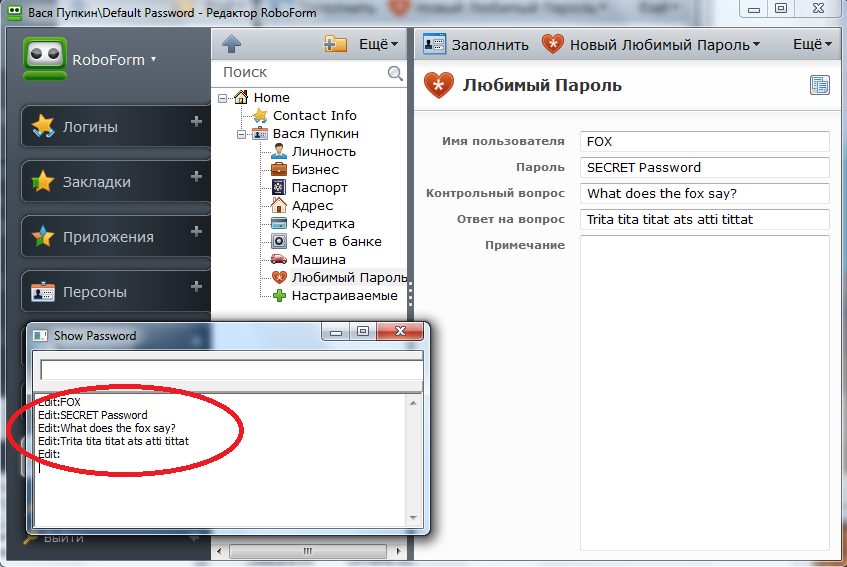
As in the previous case, Procmon pointed to the theoretical possibility of DLL Hijacking, however the creation of the working exploit was failed. So the third round is RoboForm‘s. According to the points it can be put between 1Password and KeePass, but I still would not use a password manager, which explicitly displays them on the monitor, so in my opinion, the final mark "satisfactory" is well deserved.
Summarizing
From all five password managers, only one KeePass could successfully resist all three attacks. Opened code and continued support from enthusiasts have done a really decent product. Though RoboForm and 1Password weren’t without flaws, but none of them could protect themselves from a Master Password attack. As for Sticky Password and Kaspersky Password Manager, none of them was able to protect themselves from Master Password attack. In addition, they also open up a gap in the DLL Hijacking form, so the use of passwords manager data on flash drives can be used by hackers to spread malicious code and to make an insider attack. These products require a really qualitative safety improvement. Summarizing the results of the test, we will not give preference to any one manager, as it would follow from the various subjective and personal factors; we simply looked at these password managers with regard to their safety.
Forewarned is forearmed
To protect your passwords from described interception techniques special software, which will monitor call with API-functions MARKDOWN_HASH2ab05fbef5eddf2027d7f05bdeac283dMARKDOWN_HASH and MARKDOWN_HASH84ea011a8379b1eb533f68d1d12fe6a6MARKDOWN_HASH with MARKDOWN_HASHbed4f4e4c653f53c6abf14671add9c05MARKDOWN_HASH parameters can be configured on the computer.
This opportunity is provided by some antivirus software programs, for example, in the free Firewall from COMODO, this function is set by default, in others you may have to adjust by hand. If an unauthorized access appears to application windows, Proactive Defense will give a warning window and selecting an action. However, this method does not help if you often need to use a password manager from a flash drive or on another computer. As a reliable solution a password manager, which has a protective function like UAC and blocks unauthorized access to the application, can be taken. Such a function, for example, has KeePass and 1Password.
To resolve the problem with DLL Hijacking, using special utilities on the computer we have to limit the access for writing to another applications in the appropriate folders. As in the previous paragraph, this function may be available in some anti-virus solutions. As for protection on the flash drive applications, it is not so beautiful, but you can use another step. First, the file system will convert the stick to NTFS:
convert h: /fs:ntfs /nosecurity /x
This system allows you to set security settings for individual folders and files. The rule for reading only may be created for the folder with location vulnerability, but if the file with passwords is there too, we will not be able to edit it while working on another computer. Therefore, you can create fake files with the vulnerable DLL-files and set the read only setting for them. As an extra protect passwords measure an additional binding to the key file or device may be used in the password manager. However it is necessary to know that the access to stored passwords can be vulnerable to random factors now, such as the loss of a key file and USB-device breakage.
Conclusion
Password and security may be synonyms for many people. But when there is the question of the password security, then safety comes first at once. Vendors offer a variety of solutions, which reliability at first glance is doubtful. However, password managers can hide common vulnerabilities in the advertised military codes. Do not panic and judge that you shouldn't put all your eggs in one basket, but if we decided to do it, you first need to check whether your basket is safe and secure.
Axarhöfði 14,
110 Reykjavik, Iceland














