What you should know about the Thunderstrike Mac bootkit
The first ever publicly known OS X firmware bootkit emerged out of the 31st Chaos Computer Club conference in Hamburg, Germany last month.
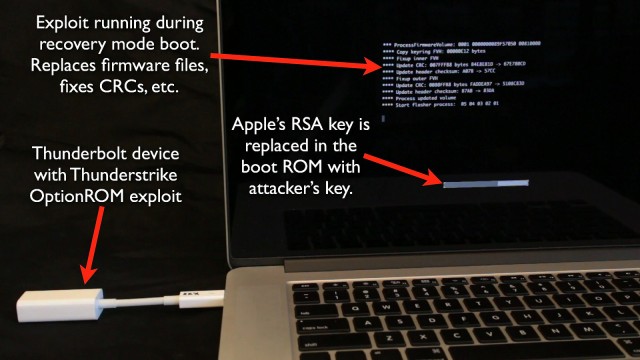
 Security researcher Trammell Hudson developed the attack and named it Thunderstrike. It exploits a vulnerability deep in the core of the Apple’s OS X operating system. In fact, the vulnerability underlies the operating system altogether. Hudson contacted Apple and they reportedly resolved the issue in all affected devices except the MacBook.
Security researcher Trammell Hudson developed the attack and named it Thunderstrike. It exploits a vulnerability deep in the core of the Apple’s OS X operating system. In fact, the vulnerability underlies the operating system altogether. Hudson contacted Apple and they reportedly resolved the issue in all affected devices except the MacBook.
There is no room for doubt here: Thunderstrike, like all boot- and rootkits, is a nasty threat that can wrest control over everything you do on your computer. You can think of it as the Ebola of computer threats: catching the disease carries devastating consequences, but the likelihood of becoming infected is relatively small.
Bootkits are a type of rootkit malware that live within the boot process beneath your computer’s operating system, commanding complete control over infected machines. They affect the Master Boot Record and initiate on startup, before the operating system even loads. Even if you delete your operating system, the bootkit remains. Bootkits, therefore, are highly resistant to removal efforts and even difficult to find, though advanced antivirus products will root them out.

Thunderstrike is a bootkit for OS X devices that can be installed via direct hardware access or through a thunderbolt connection. The first scenario, infection via direct hardware access is unlikely. Either the manufacturer would have to install the bootkit or an attacker would have to take your Macbook apart and physically install it into the hardware him or herself.
However, the second vector, infection through the Thunderbolt connection, is slightly more viable. In fact, we have a term for this kind of attack: they’re called “evil maid” attacks, or state-sponsored attacks where laptops are confiscated and examined in airports or border crossings. The same method could be applied any time you are away from your machine.
Thus, like Ebola, which is only transmittable through direct contact with bodily fluids, your machine is only susceptible to Thunderstrike if someone takes it apart or sticks a thunderbolt connection into it and installs malicious firmware on your Mac from a peripheral device.
Other pieces of malware are less impactful but have far greater transmission rates. To complete the metaphor, the common cold is airborne, and poses a far greater risk to the general public than Ebola, despite the fact that the common cold is not generally terminal.
Similarly, a piece of malware designed to eat processing power and contribute to a botnet isn’t quite as scary as Thunderstrike, but because it can infect your machine remotely through a web injection, malicious email, drive-by download or a number of other vectors, it’s actually much more of a public nuisance.
“Since it is the first OS X firmware bootkit, there is nothing currently scanning for its presence,” Hudson said. “It controls the system from the very first instruction, which allows it to log keystrokes, including disk encryption keys, place backdoors into the OS X kernel and bypass firmware passwords. It can’t be removed by software since it controls the signing keys and update routines. Reinstallation of OS X won’t remove it. Replacing the SSD won’t remove it since there is nothing stored on the drive.”
The best way to protect yourself against Thunderstrike is to make sure that no one can access your Macbook when you aren’t around. In other words, if you are careful about avoiding theft, then you should be good to go.
Axarhöfði 14,
110 Reykjavik, Iceland














