Do you save your passwords in a browser? It's not a good idea
It is better to think before you let someone borrow your computer. One of the most common risks of allowing someone else access to your desktop is that they can impersonate you, using any app where you’re already signed in.
 They could send prank message using your default email client, or profess your undying love for Justin Bieber using your logged-in Twitter account. Of course it’s annoying, but far from fatal.
They could send prank message using your default email client, or profess your undying love for Justin Bieber using your logged-in Twitter account. Of course it’s annoying, but far from fatal.
The situation becomes considerably worse if you use Google Chrome to save and synchronize passwords for easy logins at your favourite websites. An intruder who has unrestricted access to your computer for even a minute can view and copy all of your saved passwords just by visiting an easy-to-remember settings page: chrome://settings/passwords. That link opens the local copy of your saved password cache, which is synchronized to every machine where you sign in with your Google account. And the funny thing is, anyone who visits that page can see the plaintext version of every saved password just by clicking a button.
The saved password list shows the web address, username, and password for each saved set of credentials. Initially, the saved password is displayed as a row of asterisks. But if you click the masked password, you see a “Show” button that you can click to immediately display the saved password.

A malicious or spiteful intruder who can lure you away from your computer briefly can see your saved passwords, and then close the settings page. And you have no idea that your credentials have been compromised. Here’s what the attacker sees. I’ve altered the passwords and blurred crucial details in this screenshot, but it should give you a good idea of the scope of the problem:
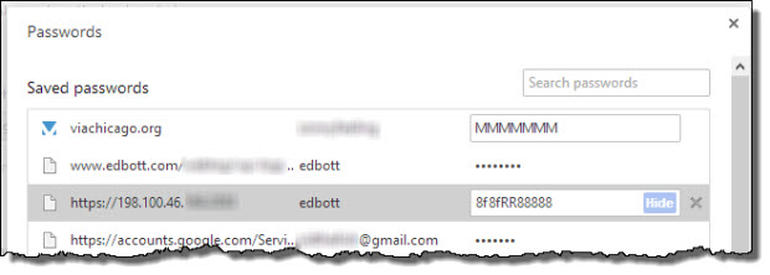
This isn’t a new feature, of course, but the issue got some publicity earlier today when software designer Elliott Kember posted a rant titled “Chrome’s insane password security strategy” at his blog. The issue got more heated and Chrome developer Justin Schuh told Kember, in essence, That’s not a bug, it’s a feature:
- I'm the Chrome browser security tech lead, so it might help if I explain our reasoning here. The only strong permission boundary for your password storage is the OS user account. So, Chrome uses whatever encrypted storage the system provides to keep your passwords safe for a locked account. Beyond that, however, we've found that boundaries within the OS user account just aren't reliable, and are mostly just theatre.
- Consider the case of someone malicious getting access to your account. Said bad guy can dump all your session cookies, grab your history, install malicious extension to intercept all your browsing activity, or install OS user account level monitoring software. My point is that once the bad guy got access to your account the game was lost, because there are just too many vectors for him to get what he wants.
- We've also been repeatedly asked why we don't just support a master password or something similar, even if we don't believe it works. We've debated it over and over again, but the conclusion we always come to is that we don't want to provide users with a false sense of security, and encourage risky behaviour. We want to be very clear that when you grant someone access to your OS user account that they can get at everything, because in effect, that's really what they get.
Perhaps he's right. But that level of attack involves preparation on the part of a hacker, as well as a nontrivial amount of technical knowledge. This avenue of access is easy and quick and leaves no audit trail. It's a vulnerability that an evil sibling can exploit to make your life miserable. It's also one that a malicious co-worker can use with devastating effect. This problem isn’t unique to Chrome. If your default browser is Firefox, you’re equally vulnerable. Anyone with physical access to your computer can click the Firefox menu, click Options, and then click the Saved Passwords button on the Security tab to get to this dialog box. No password is required to reveal all of your saved passwords in plaintext.
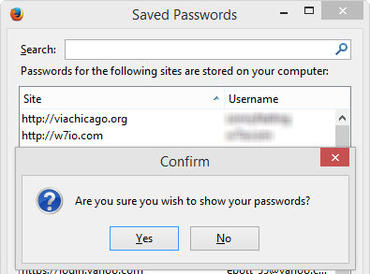
Firefox at least includes the option to set a master password, although it's not enabled by default. And if you use Mac instead of Windows do not be sure that this article is not for you, because the same easy access is available on Apple-branded devices.
Internet Explorer, on the other hand, requires an extra authentication step before you can view plaintext passwords. In Windows 7 and Windows 8, the IE password cache is stored in the Web Credential Manager. You can see your saved passwords, but clicking the Show button requires you to enter the credentials for your user account again.
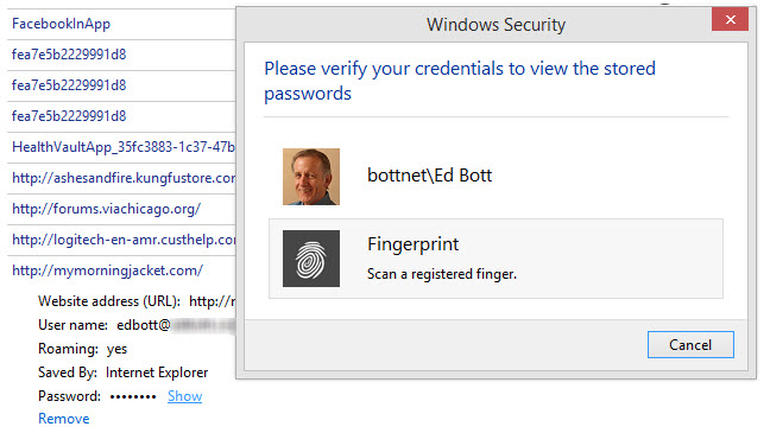
This is all, of course, an illustration of one of the most fundamental principles of computer security. If someone else has physical access to your computer, it’s not your computer anymore. You’re literally at their mercy.
If you’re worried about this issue, you should do three things:
1. Never leave your computer unlocked when you step away from the keyboard.
2. If you want to let someone borrow your computer, enable the guest account, which has limited user rights and no access to your confidential data.
3. Don’t save passwords in your browser. Use a third-party password manager instead, such as RoboForm, Lastpass, or 1Password. All of those third-party products save your credentials in encrypted stores that require you to supply credentials before accessing plaintext passwords.
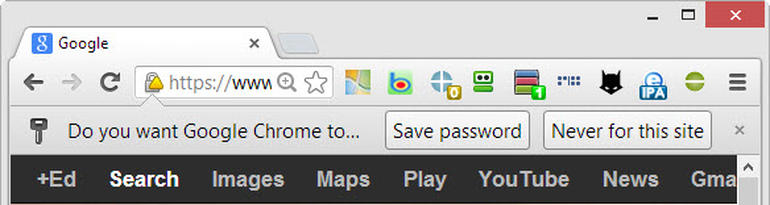
Nevertheless, Google’s developers may rethink this policy. The least they could do is explain why this is perhaps not such a great idea for customers who are vulnerable to casual attacks. Chrome aggressively encourages users to save and sync passwords, using this interface:
Axarhöfði 14,
110 Reykjavik, Iceland














