New APT groups are emerging in the Middle East
Security researchers have uncovered the first ever Arabic language advanced persistent threat (APT) group. It is impossible to determine whether Desert Falcons is state sponsored, but internet security is under threat.
 Dubbed Desert Falcons, the group of thirty or so attackers (some of whom are known by name), operates out of Palestine, Egypt and Turkey and is said to have developed and deployed their wares exclusively in the Middle East.
Dubbed Desert Falcons, the group of thirty or so attackers (some of whom are known by name), operates out of Palestine, Egypt and Turkey and is said to have developed and deployed their wares exclusively in the Middle East.
Their arsenal consists of homemade malware tools, social engineering and other techniques designed to execute and conceal campaigns on traditional and mobile operating systems. Particularly, Desert Falcons’ malware is intended to steal sensitive information from its victims, which is then used to fuel further operations and even for extortion attempts against impacted targets.
“More than 1 million files were stolen from victims,” the anti-malware company said. “Stolen files include diplomatic communications from embassies, military plans and documents, financial documents, VIP and Media contact lists and files.” The victims are targeted for secrets in their possession or intelligence information relating to their positions in governments or important organizations.
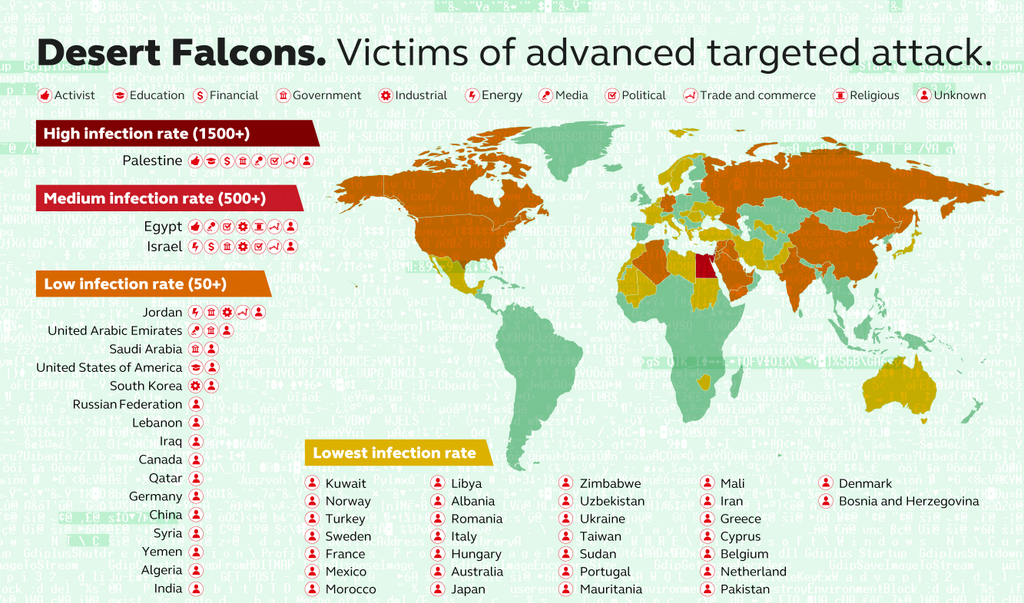
Desert Falcons’ attacks have claimed some 3000 victims in more than 50 countries. Most of those are located within Palestine, Egypt, Israel and Jordan, but there have also been discoveries in Saudi Arabia, the U.A.E., the U.S., South Korea, Morocco, and Qatar among other places.
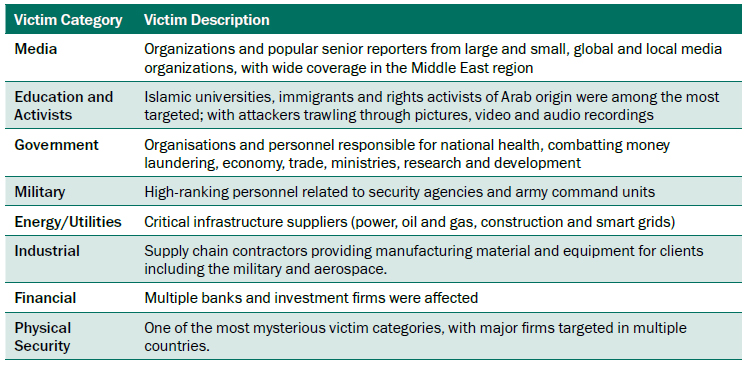
The victims include military and government organizations, employees responsible for health organizations and combating money laundering, economic and financial institutions, leading media entities, research and educational institutions, energy and utilities providers, activists and political leaders, physical security companies, and other targets that have access to important geopolitical information.
Desert Falcons' tools used in the attack include backdoors into traditional computers through which the hackers install malware capable of logging keystrokes, taking screenshots and even remotely recording audio. There is also a mobile component for Android with the capacity to spy in SMS text and call logs.
Interestingly, researchers presenting on Desert Falcons at Security Analyst Summit said these are among the first to use Facebook chats in targeted attacks, connecting with targets via common Facebook pages until gaining their trust and sending them Trojan files via a chat hidden as a photo.

This group began building its tools as early as 2011 and achieved its first infections in 2013, but it wasn’t until the end of 2014 and the beginning of 2015 that Desert Falcons’ activity really began to spike. It seems that the group is more active now than it has been at any point in the past.
Axarhöfði 14,
110 Reykjavik, Iceland














