What are the most vulnerable operating systems?
19 security vulnerabilities were reported every day in 2014. The number of vulnerabilities discovered each year in operating systems, applications, and hardware has skyrocketed in a nasty trend, according to analysis by GFI Software.
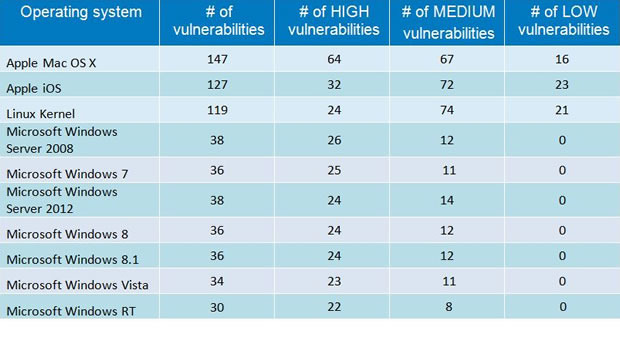
 The top spot for vulnerabilities in operating systems no longer goes to Microsoft Windows; in fact, Windows isn't even listed in the top three. Instead, the most vulnerable OS was Apple Mac OS X, followed by Apple iOS and Linux kernel.
The top spot for vulnerabilities in operating systems no longer goes to Microsoft Windows; in fact, Windows isn't even listed in the top three. Instead, the most vulnerable OS was Apple Mac OS X, followed by Apple iOS and Linux kernel.
As you can see in the list, Mac OS X had 147 vulnerabilities, with 64 being rated as high-severity bugs. There were 127 in iOS, 32 of those rated as high. Linux kernel had a rough year, with 119 security vulnerabilities and 24 being rated as high-severity. The flip-side is that none of the security holes in Windows versions were rated as low severity. "2014 was a tough year for Linux users from internet security point of view, coupled with the fact that some of the most important security issues of the year were reported for applications that usually run on Linux systems," explained GFI Software manager Cristian Florian.
"Heartbleed, for example, is a critical security vulnerability detected in OpenSSL while Shellshock is a vulnerability that affects GNU Bash." However, Microsoft can't crow too much about being "more secure," since Internet Exploder Explorer blew away the "competition" by having nearly twice as many security flaws than the second most vulnerable app, which was Google Chrome. IE had 242 security flaws, with a whopping 220 of those being high-severity vulnerabilities. Chrome had 124 total bugs with 86 of those rated as high. With a 117 total, Firefox wasn't too far behind Chrome for security holes reported, but only 57 were high severity.
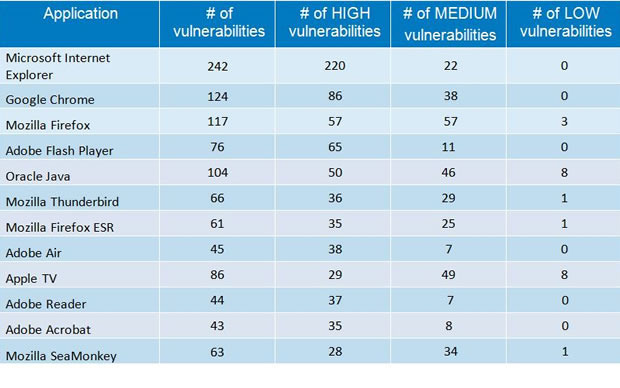
It's interesting to note that a separate report on security flaws by Secunia found that Google Chrome was the most vulnerable in January 2015; Chrome had 71, compared to the second place tie of 19 security glitches each in Oracle Java JRE and Oracle Java JDK. Internet Explorer didn't even make the top 20 list for vulnerabilities discovered in the first month of this year. Unsurprisingly, GFI said the worst offender in 2014 for having security flaws was third-party applications. Apps made up a whopping 83% of reported bugs, followed by 13% in operating systems and then 4% in hardware.
Florian reported: “The applications listed here are pretty much the same as in 2013. Not surprisingly at all, web browsers continue to have the most security vulnerabilities because they are a popular gateway to access a server and to spread malware on the clients. Adobe free products and Java are the main challengers but web browsers have continuously topped the table for the last six years. Mozilla Firefox had the most vulnerabilities reported in 2009 and 2012; Google Chrome in 2010 and 2011; Internet Explorer was at the top for the last two years.” To review, last year an average of 19 new security vulnerabilities were reported every day to the National Vulnerability Database (NVD).
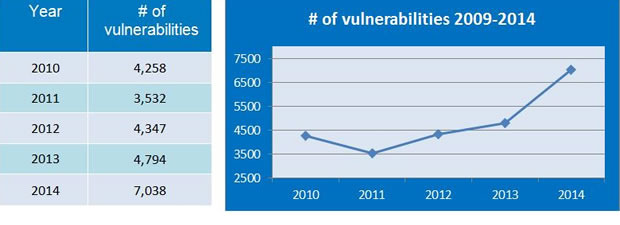
In total, there were 7,038 vulnerabilities in 2014. That figure blows away the new flaws found in any other year. For comparison, in 2013 there were 13 new security vulnerabilities per day for a total of 4,794; at that time, the number was the highest number of vulnerabilities in the last five years.
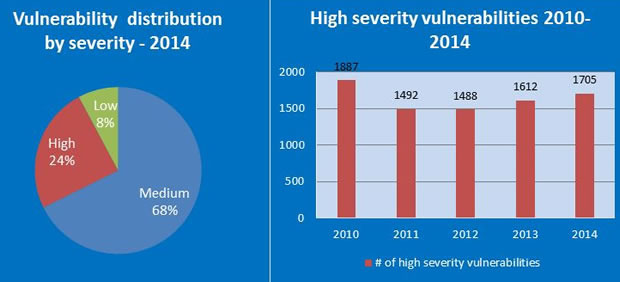
If you'd like to end with "good" news, then GFI found some in the fact that the percentage of vulnerabilities rated as "high severity" dropped to 24% in 2014. Although that is lower than in 2013, there were still more total vulnerabilities discovered in 2014. Sixty-eight percent of vulnerabilities in 2014 were rated as "medium" for severity, with only 8% rated as "low."
Axarhöfði 14,
110 Reykjavik, Iceland














