Cybercrime gang uses Google services for malware command and control
An organised cybercriminal gang is using Google services to issue command and control (C&C) communications to help monitor and control the machines of unsuspecting malware victims.
 The Carbanak hacking group is one of the most successful cybercriminal operations in the world. Since it started operating in 2013, the gang has attacked banks, e-payment systems and financial institutions across the globe using Trojan malware in a stealthy and continuous campaign, making off with a suspected total of over $1 billion in stolen funds.
The Carbanak hacking group is one of the most successful cybercriminal operations in the world. Since it started operating in 2013, the gang has attacked banks, e-payment systems and financial institutions across the globe using Trojan malware in a stealthy and continuous campaign, making off with a suspected total of over $1 billion in stolen funds.
Carbanak - also known as Anunak - is a highly organised group and continually evolves its tactics in order to continue to carry out cybercrime while avoiding detection by potential targets and the authorities. The latest malicious scheme by the group - dubbed Digital Plagiarist - sees the group using office documents hosted on mirrored domains in order to distribute the malware. This instance of malware is distributed using the common method of hiding a malicious document - this time disguised as an RTF file - inside a phishing email. However, what that malicious file executes code to do is what's new.
Cybersecurity researchers at Forcepoint have pointed out that the Carbanak group's VBScript malware contains additional script - 'ggldr' - which is capable of using Google services as a command and control channel. This allows hackers to send and receive commands to and from Google Apps Script, Google Sheets, and Google Forms services.
A unique Google Sheets spreadsheet is dynamically created, allowing systems to easily manage each infected victim, like checking on the status of the infected machine or sending command and control check ins. The cycle uses the Google script to continuously repeat, as demonstrated in the image below.
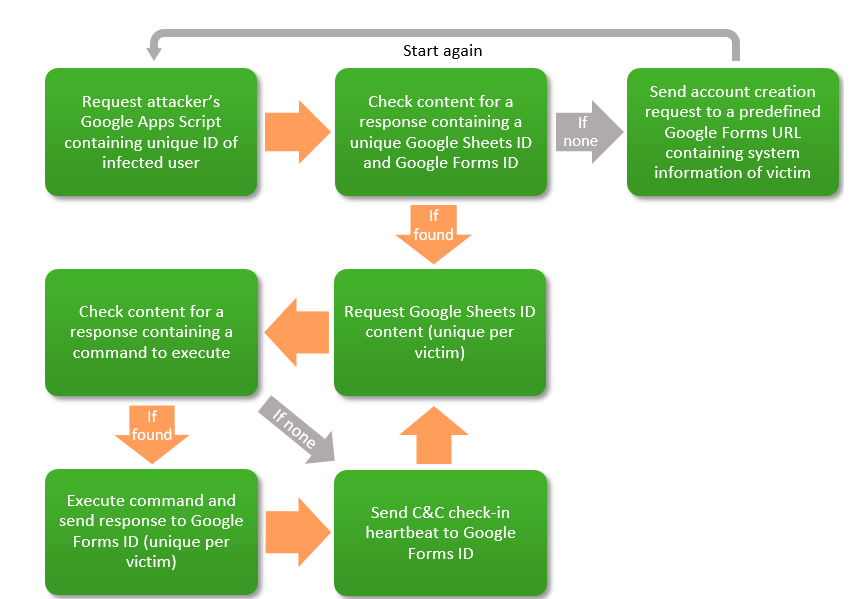
Forcepoint researchers warn that using Google as an independent C&C channel is likely to be more successful than using newly created domains or domains with no reputation. The cybersecurity researchers say they've notified Google of the issue - experts asked Google for comment, but hadn't received a reply at the time of publication.
Axarhöfði 14,
110 Reykjavik, Iceland














