New fileless malware uses DNS queries to receive PowerShell commands
It is no secret that cybercriminals are becoming dramatically more adept, innovative, and stealthy with each passing day.
 While new forms of cybercrime are on the rise, traditional activities seem to be shifting towards more clandestine techniques that involve the exploitation of standard system tools and protocols, which are not always monitored.
While new forms of cybercrime are on the rise, traditional activities seem to be shifting towards more clandestine techniques that involve the exploitation of standard system tools and protocols, which are not always monitored.
The latest example of such attack is DNSMessenger – a new Remote Access Trojan (RAT) that uses DNS queries to conduct malicious PowerShell commands on compromised computers – a technique that makes the RAT difficult to detect onto targeted systems. The Trojan came to the attention of Cisco's Talos threat research group by a security researcher named Simpo, who highlighted a tweet that encoded text in a PowerShell script that said 'SourceFireSux.' SourceFire is one of Cisco's corporate security products.
DNSMessenger Attack Is Completely Fileless
Further analysis of the malware ultimately led Talos researchers to discover a sophisticated attack comprising a malicious Word document and a PowerShell backdoor communicating with its command-and-control servers via DNS requests. Distributed through an email phishing campaign, the DNSMessenger attack is completely Fileless, as it does not involve writing files to the targeted system; instead, it uses DNS TXT messaging capabilities to fetch malicious PowerShell commands stored remotely as DNS TXT records.
This feature makes it invisible to standard anti-malware defenses. PowerShell is a powerful scripting language built into Windows that allows for the automation of system administration tasks. The malicious Word document has been crafted "to appear as if it were associated with a secure e-mail service that is secured by McAfee," according to a blog post published by Talos researchers Edmund Brumaghin and Colin Grady on Thursday.
Here's How the DNSMessenger attack Works:
When opened, the document launches a Visual Basic for Applications (VBA) macro to execute a self-contained PowerShell script in an attempt to run the backdoor onto the target system. What's interesting? Everything, until this point, is done in memory, without writing any malicious files to the system's disk.
Next, the VBA script unpacks a compressed and sophisticated second stage of PowerShell, which involves checking for several parameters of the target environment, like the privileges of the logged-in user and the version of PowerShell installed on the target system. This information is then used to ensure persistence on the infected host by changing the Windows Registry and installing a third stage PowerShell script that contains a simple backdoor.
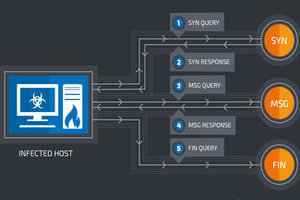
The backdoor is being added to the Windows Management Instrumentation (WMI) database, if the victim does have administrative access, allowing the malware backdoor to stay persistent on the system even after a reboot. The backdoor is an additional script that establishes a sophisticated 2-way communications channel over the Domain Name System (DNS) – usually used to look up the IP addresses associated with domain names, but has support for different types of records.
The DNSMessenger malware backdoor uses DNS TXT records that, by definition, allows a DNS server to attach unformatted text to a response. The backdoor periodically sends DNS queries to one of a series of domains hard-coded in its source code. As part of those requests, it retrieves the domain's DNS TXT record, which contains further PowerShell commands that are executed but never written to the local system.
Now, this "fourth stage" Powershell script is the actual remote control tool used by the malware attacker. This script queries the command-and-control servers via DNS TXT message requests to ask what commands to execute. Any command received is then executed, and the output is communicated back to the C&C server, allowing the attacker to execute any Windows or application commands on the infected system.
All attackers need to do is leave malicious commands and instructions inside the TXT records of their domains, which, when queried, is executed via the Windows Command Line Processor, and the output is sent back as another DNS query. The domains registered by the DNSMessenger RAT are all down, so till now, it is not known that what types of commands the attackers relayed to infected systems. However, the researchers say this particular RAT was used in a small number of targeted attacks.
This is not the first time when the researchers came across a Fileless malware. At early last month, Kaspersky researchers also discovered fileless malware, that resides solely in the memory of the compromised computers, targeting banks, telecommunication companies, and government organizations in 40 countries.
Axarhöfði 14,
110 Reykjavik, Iceland














