Ztorg Trojan: Infect yourself for 5 cents
A lot of ads on the Internet promote easy ways to earn money.
 They tend to lead to fishy places — say, a post from an alleged mother of three who stays at home, earning several thousand dollars a day, and says you can do the same. But there are other ways to earn some easy money, too, that may seem much more plausible.
They tend to lead to fishy places — say, a post from an alleged mother of three who stays at home, earning several thousand dollars a day, and says you can do the same. But there are other ways to earn some easy money, too, that may seem much more plausible.
For example, some services offer to pay you for installing apps. The money amounts to pocket change — about 5 cents per app — but the work is pretty effortless, so some people find it attractive nonetheless. This kind of scheme is especially popular among children — install 50 apps and get a $2.50 to buy some gear for your favorite character in an online game.
The Google Play app store has quite a few applications that are in fact app exchanges. You download one of those, install it, see a list of apps for which you can get paid, download a couple of those on the list, install them, play a couple of minutes — and profit!
That looks rather mundane — even legitimate. Indeed, many software developers place a high value on the number of app downloads, and such a scheme increases that number, even if it isn’t exactly honest. No wonder developers are willing to pay for it. There doesn’t seem to be a catch — or is there?
Money for nothing, malware for free
Of course there is — otherwise, why would we write about it? It turns out that, among other things, such app exchanges may urge you to download malware, in particular the infamous Ztorg Trojan. That’s the Trojan downloaded from Google Play 500,000 times disguised as a guide for the popular game Pokémon Go.
Guide for Pokémon Go is not the only app containing Ztorg. Roman Unuchek, the Kaspersky Lab expert who discovered Ztorg in the app, explored the applications distributed via these exchanges for several months. He found out that every month new apps appeared that were in fact just a disguise for Ztorg.
The app could be a photo editor, a compass, a game — anything. The perpetrators did not even try adding malicious code to a useful existing application. Instead, they wrote malicious apps from scratch. As a result, some of them are useless — for example, one simply scrolls through images, informing you that it’s “loading, please wait” and evidently doing nothing more — except infecting your smartphone with the Ztorg Trojan.
What Ztorg actually does
All of these applications have two things in common. First, their download numbers increase rapidly — by tens of thousands per day. Second, if you look at their user reviews in the Google Play store, most mention that people downloaded those apps for money, credits, bonuses, or something like that.
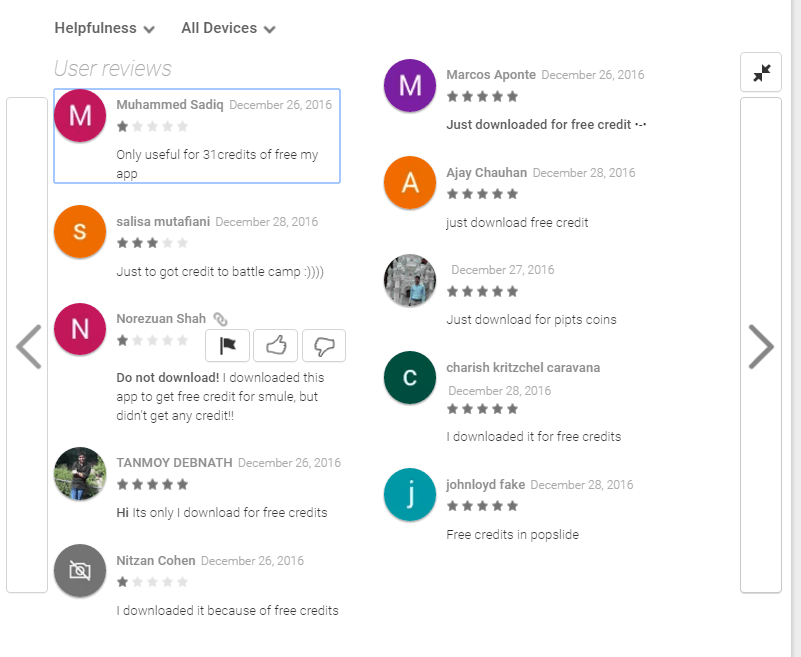
The Ztorg Trojan hasn’t changed. After installation, it collects information about the system and the device and sends it to the command-and-control (C&C) server. The server responds with files that enable the malware to gain root access to the device, after which crooks have the freedom to do whatever they want: show ads, download other Trojans, whatever.
Ztorg also spreads through ads. You click on a banner and download the app, install it, and get infected. Very easy!
What’s interesting is that Ztorg shows its victims ads from the very same networks through which it spreads itself. The networks are legitimate; many other applications use them to try to monetize themselves. It’s just that the networks’ security guys missed the important point that they were advertising malware.
To be fair, Ztorg’s developers hid the malicious functionality, and it is not evident when studying the app. For example, Ztorg evaluates its environment and won’t run in a sandbox (a test environment).
Most malvertising banners do not link directly to the app download page but rather take users to a page that redirects to another page, which redirects to another page, and then to another page — all for the sake of obfuscation. Unuchek counted up to 27 such redirects before finally getting to the download. Moreover, the app can delay downloading malicious files from the C&C server for up to 90 minutes — by that time a tester would probably have decided that the app wasn’t doing anything malicious.
Actually, obfuscation is what got the malicious applications into the official Google Play store. Other Trojans lurk in there as well — we’ve already covered that topic (more than once) — so you should not blindly trust all applications from this or any store.
The moral
How can you avoid becoming a victim of such attacks and letting scammers into your phone? We have two tips for you:
1. Download applications only from trustworthy developers or, better, from official app stores. You still may encounter Trojans, but they are far less prevalent in official stores.
2. Install reliable protection.
Download SafeUM — communicate privately, without advertising and spam.
Axarhöfði 14,
110 Reykjavik, Iceland

















