Chthonic Zeus variant targeting online bank users
Researchers have uncovered a new variant of the infamous Zeus Trojan. It’s called Chthonic, a reference to spirits and deities from the underworld in Greek mythology, and it’s targeting 150 banks and 20 payment systems in 15 countries.
 Zeus, as its name suggests, is the king of banking malware. It first emerged in 2007 and has been wreaking havoc on online bank accounts ever since. In 2011, its developers threw in the towel and posted its source code for all to see. It may seem as though this would be the end for Zeus, but, in fact, the opposite is true.
Zeus, as its name suggests, is the king of banking malware. It first emerged in 2007 and has been wreaking havoc on online bank accounts ever since. In 2011, its developers threw in the towel and posted its source code for all to see. It may seem as though this would be the end for Zeus, but, in fact, the opposite is true.
The disclosure of the Zeus source-code has empowered criminal programmers to create scores of variations on its highly customizable framework such as GameOver, Zitmo and a number of other threats. After infecting its host machine, Chthonic collects system information, steals saved passwords, logs keystrokes, grants remote computer access to its controllers and also has the capacity to remotely activate cameras and audio recorders on infected machines.
Like earlier banking Trojans, Chthonic deploys malicious web injection techniques in order to replace legitimate banking interfaces with custom imagery and code. Unwitting online banking customers then willingly hand their banking credentials over to the criminals behind the malware, not realizing that their banking login page has been replaced by a malicious lookalike. One advantage to this method is that the bad guys are also able to steal second factors of authentication, like one-time passwords and SMS codes, as the user enters them into their compromised browser in real time.
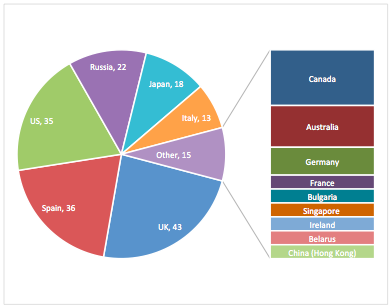
Chthonic is mainly targeting institutions in the United Kingdom, Spain, the United States, Russia, Japan and Italy. In Japan, the malware is overriding bank security warnings with a script that allows the attackers to perform transactions on the users account. In Russia, infected users can’t even access their banking site because Chthonic injects an iframe that redirects users to a fake, albeit convincing, phishing page.
However, before the actual theft of banking credentials occurs, the user must first become infected with the Chthonic malware itself. As is so often the case with any malware, Chthonic infiltrates user-machines via malicious Web links and email attachments. In either case, the attack downloads a malicious .DOC file to its victim’s machine. That document contains rich text format code that exploits a remote code execution flaw in Microsoft Office that was fixed back in April. The malware won’t work on properly updated machines.
Axarhöfði 14,
110 Reykjavik, Iceland














