Joomla targeted in WordPress campaign that delivers TeslaCrypt
 Strains of ransomware have been detected on Joomla domains, revealing a disturbing evolution of the malware's attack vectors. According to Brad Duncan, attacks based on the "admedia" campaign have shifted from the traditional target of websites supported by the WordPress content management system, and instead, have graduated to also hunt down vulnerable Joomla CMS Web domains.
Strains of ransomware have been detected on Joomla domains, revealing a disturbing evolution of the malware's attack vectors. According to Brad Duncan, attacks based on the "admedia" campaign have shifted from the traditional target of websites supported by the WordPress content management system, and instead, have graduated to also hunt down vulnerable Joomla CMS Web domains.
The strings revealed an admedia iframe injection which led not only to the installation of multiple backdoors, but the admedia malicious domains generated on these sites sent unwitting visitors to an exploit kit containing the TeslaCrypt ransomware.
Read moreTeslaCrypt flaw allows free file decryption
 TeslaCrypt, a ransomware family that emerged roughly a year ago, includes a design flaw that has already allowed security researchers build a free file decryption tool. The issue affects TeslaCrypt and TeslaCrypt 2.0 variants of the malware and resides in the encryption key storage algorithm.
TeslaCrypt, a ransomware family that emerged roughly a year ago, includes a design flaw that has already allowed security researchers build a free file decryption tool. The issue affects TeslaCrypt and TeslaCrypt 2.0 variants of the malware and resides in the encryption key storage algorithm.
The issue has been fixed in TeslaCrypt 3.0, but files encrypted with the older versions of the ransomware can be decrypted without paying cybercriminals to do so. Spotted in late February 2015, the ransomware was found to encrypt not only photos, videos, and documents, but files associated with video games as well.
Read moreMassive ransomware campaign using TeslaCrypt discovered
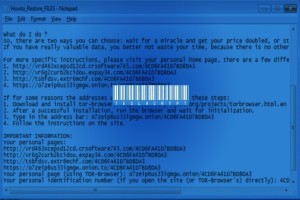 In the past few days, a new version of the TeslaCrypt ransomware was released, and security researchers have now detected a massive spam campaign distributing this new threat.
In the past few days, a new version of the TeslaCrypt ransomware was released, and security researchers have now detected a massive spam campaign distributing this new threat.
The first signs of something out of the ordinary were initially spotted on the Bleeping Computer forums, where users started complaining about being infected with ransomware. After further analysis by community members, the ransomware proved to be a new TeslaCrypt version that added minor changes to its code, but these were more than enough to prevent users from using the TeslaDecoder to decrypt their files.
Read moreTeslaCrypt 2.0 ransomware: stronger and more dangerous
 Cybercriminals are learning from each other. Take TeslaCrypt, for example. It is a relatively new family of ransomware; its samples were first detected in February 2015.
Cybercriminals are learning from each other. Take TeslaCrypt, for example. It is a relatively new family of ransomware; its samples were first detected in February 2015.
The notable feature of the early TeslaCrypt versions was that malware was targeting not only usual sets of files, including documents, pictures and videos, but games-related file types as well. By that time, it was a rather weak malware due to a couple of its technical flaws. Despite the fact malware creators scared their victims with the frightful RSA-2048 algorithm, in reality the encryption was not that strong.
Read moreComputer gamers targeted by ransomware
 Gamers come in all ages and from all walks of life; they may or may not have files they feel are irreplaceable enough as to be tempted to pay a ransom to get those files decrypted. But what if it was your saved games and your Steam account that was encrypted and held for ransom?
Gamers come in all ages and from all walks of life; they may or may not have files they feel are irreplaceable enough as to be tempted to pay a ransom to get those files decrypted. But what if it was your saved games and your Steam account that was encrypted and held for ransom?
That’s exactly what the crypto-ransomware is doing: in fact it targets over 50 file extensions related to video games including Steam, single and multiplayer games, and even game development software. Although the ransom window which announces “your personal files are encrypted” may look like CryptoLocker, don’t be fooled.
Read more New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
Axarhöfði 14,
110 Reykjavik, Iceland














