FLocker ransomware now targeting Smart TVs
 Trend Micro researchers have found the first major example of ransomware that can attack a Smart TV with hackers using an updated version of FLocker that targets devices running the Android operating system.
Trend Micro researchers have found the first major example of ransomware that can attack a Smart TV with hackers using an updated version of FLocker that targets devices running the Android operating system.
Trend Micro researcher wrote that this FLocker version, one of more than 7,000 variants that have been tracked by the company since the malware was first spotted in May 2015, has the ability to infect and lock the screen of any device running the Android operating system, including a Smart TV. This FLocker operates as a police Trojan and attempts to scare the victim into paying by claiming to be the “US Cyber Police.”
Read moreResearcher uses Regsvr32 function to bypass AppLocker
 For years, business-focused versions of Windows have had an AppLocker feature that lets you blacklist or whitelist apps. It's undoubtedly helpful for companies eager to keep malware or just risky software off their network.
For years, business-focused versions of Windows have had an AppLocker feature that lets you blacklist or whitelist apps. It's undoubtedly helpful for companies eager to keep malware or just risky software off their network.
A researcher in Colorado has discovered a feature in Regsvr32 that allows an attacker to bypass application whitelisting protections, such as those afforded by Microsoft's AppLocker. If the technique is used, there's little evidence left behind for investigators, as the process doesn't alter the system registry and in some cases comes across as normal Internet Explorer traffic.
Read moreCTB-Locker ransomware infects thousands of web servers
 In last few years, we saw an innumerable rise in ransomware threats ranging from Cryptowall to Locky ransomware discovered last week.
In last few years, we saw an innumerable rise in ransomware threats ranging from Cryptowall to Locky ransomware discovered last week.
Now, another genre of ransomware had been branched out from the family of CTB-Locker Ransomware with an update to infect "Websites". The newly transformed ransomware exclusively hijacks the websites by locking out its data, which would only be decrypted after making a payment. This seems to be the very first time when any ransomware has actually defaced a website in an attempt to convince its administrator to comply with the ransom demand.
Read moreRansomware resets PIN and permanently locks your smartphones
 Malicious apps that disable Android phones until owners pay a hefty ransom are growing increasingly malevolent and sophisticated as evidenced by a newly discovered sample that resets device PIN locks, an advance that requires a factory reset.
Malicious apps that disable Android phones until owners pay a hefty ransom are growing increasingly malevolent and sophisticated as evidenced by a newly discovered sample that resets device PIN locks, an advance that requires a factory reset.
The app first tricks inexperienced users into granting it device administrator privileges. To achieve this, it overlays a bogus patch installation window on top of an activation notice. When targets click on the continue button, they really grant the malicious app elevated rights that allow it to make changes to the Android settings.
Read moreAndroid ransomware campaign hits tens of thousands of devices
 A new variant of mobile ransomware that encrypts the content of Android smartphones is putting a new spin on both how it communicates with its masters and how it spurs its victims into action.
A new variant of mobile ransomware that encrypts the content of Android smartphones is putting a new spin on both how it communicates with its masters and how it spurs its victims into action.
The updated version of Simplocker masquerades on app stores and download pages as a legitimate application, and uses an open instant messaging protocol to connect to command and control servers. The malware requests administrative permissions to sink its hooks deep into Android. Once it's installed, it announces itself to some victims by telling them it was planted by the NSA — and to get their files back, they'll have to pay a fine.
Read moreComputer gamers targeted by ransomware
 Gamers come in all ages and from all walks of life; they may or may not have files they feel are irreplaceable enough as to be tempted to pay a ransom to get those files decrypted. But what if it was your saved games and your Steam account that was encrypted and held for ransom?
Gamers come in all ages and from all walks of life; they may or may not have files they feel are irreplaceable enough as to be tempted to pay a ransom to get those files decrypted. But what if it was your saved games and your Steam account that was encrypted and held for ransom?
That’s exactly what the crypto-ransomware is doing: in fact it targets over 50 file extensions related to video games including Steam, single and multiplayer games, and even game development software. Although the ransom window which announces “your personal files are encrypted” may look like CryptoLocker, don’t be fooled.
Read moreCTB-Locker is the newest crypto malware
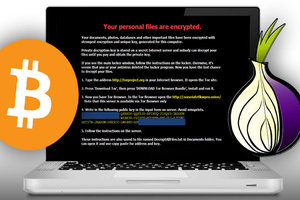 From late 2013 through the first half of 2014, CryptoLocker malware was a major concern for many businesses and individuals. The FBI was able to successfully disrupt CryptoLocker, along with Game Over Zeus, but according to the figures in their legal complaint against Evgeniy Bogachev, not before his malware had encrypted a lot of computers.
From late 2013 through the first half of 2014, CryptoLocker malware was a major concern for many businesses and individuals. The FBI was able to successfully disrupt CryptoLocker, along with Game Over Zeus, but according to the figures in their legal complaint against Evgeniy Bogachev, not before his malware had encrypted a lot of computers.
The second major Crypto Malware was CryptoWall. In Malcovery's 3rd Quarter malware report, there were documented 24 separate spam campaigns that resulted in CryptoWall infections. Today we may have seen the beginning of the Next Wave of Crypto Malware being delivered by spam.
Read more New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
Axarhöfði 14,
110 Reykjavik, Iceland














