A serious Siri bug on iOS 11 exposes all of your hidden messages
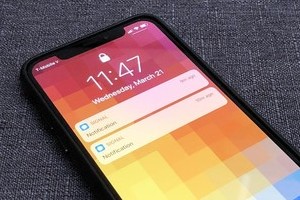 On iOS 11, Apple introduced a new way to protect user privacy by letting you hide the contents of your notifications on your iPhone's lock screen until you unlock the device with Touch ID or Face ID.
On iOS 11, Apple introduced a new way to protect user privacy by letting you hide the contents of your notifications on your iPhone's lock screen until you unlock the device with Touch ID or Face ID.
But it turns out there's a very simple way to read these hidden notifications even if you can't unlock the phone: Just ask Siri to read them to you. Yep, that's right: A new bug reveals that you can simply ask Siri to spy on someone's hidden notifications. Even with the "Show Previews" featured set to display only "When Unlocked" (Settings > Notifications > Show Previews), you can still ask Siri to read any hidden notifications out loud by saying "Hey Siri, read my notifications."
Read moreThe Feds can now unlock every iPhone model in existence
 In what appears to be a major breakthrough for law enforcement, and a possible privacy problem for Apple customers, a major U.S. government contractor claims to have found a way to unlock pretty much every iPhone on the market.
In what appears to be a major breakthrough for law enforcement, and a possible privacy problem for Apple customers, a major U.S. government contractor claims to have found a way to unlock pretty much every iPhone on the market.
Cellebrite, a Petah Tikva, Israel-based vendor that's become the U.S. government's company of choice when it comes to unlocking mobile devices, is this month telling customers its engineers currently have the ability to get around the security of devices running iOS 11. That includes the iPhone X.
Read moreNew bug can cause iMessage to crash with a text message
 There's a new bug floating around called "chaiOS" that appears to be a basic GitHub link. However, when you text it to a person via the iMessage app, it will crash the app and possibly cause the device to freeze and restart.
There's a new bug floating around called "chaiOS" that appears to be a basic GitHub link. However, when you text it to a person via the iMessage app, it will crash the app and possibly cause the device to freeze and restart.
In other words: Be aware that this exists, but don't send it to anyone. It was Twitter user Abraham Masri who first uncovered the bug. The people tested it out, and it certainly messed up their devices. They reported crashes and severe lags as a result of the bugs that persisted until the thread containing the link was deleted from the iMessage app.
Read moreApple says Meltdown and Spectre flaws affect all Mac and iOS devices
 Apple’s iPhones, iPads and Mac computers are all vulnerable to the major processor flaws revealed on Wednesday, the company has warned, but it says updates are already available.
Apple’s iPhones, iPads and Mac computers are all vulnerable to the major processor flaws revealed on Wednesday, the company has warned, but it says updates are already available.
The flaws known as Meltdown and Spectre affect almost every modern computing device from all manufacturers using chip designs from Intel, AMD and ARM. Apple uses Intel processors in its Mac computers and ARM-based designs for its A-series processors used in the iPhone, iPad, Apple TV and Apple Watch lines. Apple said: “All Mac systems and iOS devices are affected, but there are no known exploits impacting customers at this time.”
Read moreGoogle Project Zero 'tpf0' exploit whets appetite for iOS 11 jailbreak
 Google's Project Zero iOS bug hunter Ian Beer has released details about an iOS 11 exploit that could offer up a jailbreak for iOS 11.1.2. Beer last week teased that he had an exploit called 'tfp0', which is short for the kernel task port in iOS, and has today followed with an exploit using two recently patched flaws that may offer the rare prospect of a possible jailbreak on iOS.
Google's Project Zero iOS bug hunter Ian Beer has released details about an iOS 11 exploit that could offer up a jailbreak for iOS 11.1.2. Beer last week teased that he had an exploit called 'tfp0', which is short for the kernel task port in iOS, and has today followed with an exploit using two recently patched flaws that may offer the rare prospect of a possible jailbreak on iOS.
It appears what he has released isn't a full jailbreak but enough to allow security researchers to bypass software restrictions imposed by Apple and test a newish version of iOS. It may also help create a jailbreak for those interested in testing iOS 11.1.2 or below.
Read moreWith camera permission, iPhone apps can take pictures and videos without noticing
 Whenever you give iPhone apps permission to access your camera, the app can surreptitiously take pictures and videos of you as long as the app is in the foreground, a security researcher warned on Wednesday.
Whenever you give iPhone apps permission to access your camera, the app can surreptitiously take pictures and videos of you as long as the app is in the foreground, a security researcher warned on Wednesday.
Felix Krause, who recently warned of the danger of malicious iPhone password popups, wrote a blog post as a sort of PSA for iPhone users. To be clear, this is not a bug, but likely intended behavior. What this means is that even if you don't see the camera "open" in the form of an on-screen viewfinder, an app can still take photos and videos. It is unknown how many apps currently do this, but Krause created a test app as a proof-of-concept.
Read moreiOS 11 security bug allows hackers to bypass iPhone passcode, access photos
 A bug that has been confirmed on both iOS 11 and iOS 11.1 beta allows hackers to bypass the passcode of an iPhone and access the photos stored in the gallery by simply dialing your phone number.
A bug that has been confirmed on both iOS 11 and iOS 11.1 beta allows hackers to bypass the passcode of an iPhone and access the photos stored in the gallery by simply dialing your phone number.
Discovered by YouTube iDeviceHelp, this bug can be exploited by dialing the phone number of the locked iPhone. To gain unauthorized access, the exploit also involves invoking Siri, so if the digital assistant is disabled on your device, you’re on the safe side. As you can see for yourselves in the video at the end of the article, the method is quite complex and even though it’s hard to believe that someone would discover it by mistake.
Read moreBeware of sketchy iOS popups that want your Apple ID
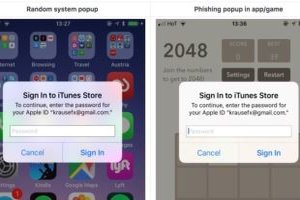 One of iOS' rougher edges are the popups it produces on a regular but seemingly random basis. These popups require users to enter their Apple ID before they can install or update an app or complete some other mundane task.
One of iOS' rougher edges are the popups it produces on a regular but seemingly random basis. These popups require users to enter their Apple ID before they can install or update an app or complete some other mundane task.
The prompts have grown so common most people don't think twice about them. Mobile app developer Felix Krause makes a compelling case that these popups represent a potential security hole through which attackers can steal user credentials. In a blog post published Tuesday, he showed side-by-side comparisons, pictured above, of an official popup produced by iOS and a proof-of-concept phishing popup.
Read moreApps and hacks to help improve your mobile security
 Just like any other digital device that can connect to the internet, your mobile phone poses a security threat if you don’t take the steps required to protect it. With so many new apps being released in the Apple App Store and the Google Play Store every day, it’s difficult to know which ones can be trusted.
Just like any other digital device that can connect to the internet, your mobile phone poses a security threat if you don’t take the steps required to protect it. With so many new apps being released in the Apple App Store and the Google Play Store every day, it’s difficult to know which ones can be trusted.
There have been plenty of reports of users installing apps on their phones which can then do anything from track everything you type to taking control of your camera without your knowledge. This is a seriously scary prospect if you value your privacy and don’t want identity thieves to be able to steal your identity or bank details.
Read moreWhatsApp, WinZip among the most blacklisted apps in the enterprise
 WhatsApp Messenger, WinZip, and Where's My Droid Pro have made the list for the most blacklisted iOS and Android apps in enterprise environments.
WhatsApp Messenger, WinZip, and Where's My Droid Pro have made the list for the most blacklisted iOS and Android apps in enterprise environments.
Mobile security firm Appthority launched the latest Enterprise Mobile Security Pulse Report, a glimpse into how enterprise players tackle mobile security and network threats by banning apps considered to be a threat from accessing corporate resources and platforms. Corporations can blacklist mobile applications for a variety of reasons. Known security holes and vulnerabilities or ways for confidential information to be leaked, a lack of secure communication and encryption.
Read moreAxarhöfði 14,
110 Reykjavik, Iceland















