Samsung joins the self-driving car gold rush
 The tech industry has a bad case of four-wheel fever, and it looks like there's no cure in sight. Before too long, it will be impossible to buy a new car without an embedded LTE modem—ostensibly there for our convenience, but with the side effect of creating a new revenue stream from monetized data.
The tech industry has a bad case of four-wheel fever, and it looks like there's no cure in sight. Before too long, it will be impossible to buy a new car without an embedded LTE modem—ostensibly there for our convenience, but with the side effect of creating a new revenue stream from monetized data.
And then there's the self-driving car gold rush. Anyone who's anyone in the tech or automotive worlds is working on an autonomous vehicle, a list that now includes Samsung. The company has been granted permission by the South Korean government to begin testing an autonomous vehicle on public roads.
Read moreHere’s North Korea’s totalitarian Android tablet
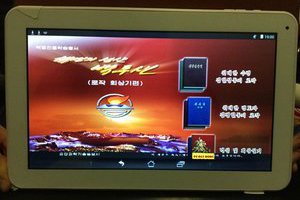 When you think of North Korea, the first thing that springs to mind is probably not a well-featured tablet PC. But that's just what researchers at the Chaos Communication Congress hacking festival revealed on Tuesday.
When you think of North Korea, the first thing that springs to mind is probably not a well-featured tablet PC. But that's just what researchers at the Chaos Communication Congress hacking festival revealed on Tuesday.
Called Woolim, this tablet is designed to limit the distribution of contraband media, track its users, and generally act as a propaganda platform for the Democratic People's Republic of Korea. “It's pretty locked down,” researcher Florian Grunow told in an interview on Tuesday. Grunow presented the research along with co-researchers Niklaus Schiess and Manuel Lubetzki. Woolim is a small, white Android device that looks like a fairly standard tablet.
Read moreNorth Korea hacks South's military cyber command
 South Korea's military cyber command, set up to guard against hacking, appears to have been breached by North Korea, the military has said. A spokesman told that classified information was thought to have been stolen, although it is not clear exactly what data was accessed.
South Korea's military cyber command, set up to guard against hacking, appears to have been breached by North Korea, the military has said. A spokesman told that classified information was thought to have been stolen, although it is not clear exactly what data was accessed.
The North has previously been accused of hacking into banks and media outlets but never the South's military. Pyongyang has in the past rejected allegations of cyber crime involvement. "It seems the intranet server of the cyber command has been contaminated with malware. We found that some military documents, including confidential information, have been hacked," a military spokesman told.
Read moreNorth Korea mounts long-running hack of South Korea computers
 North Korea hacked into more than 140,000 computers at 160 South Korean firms and government agencies, planting malicious code under a long-term plan laying groundwork for a massive cyber attack against its rival, police in the South said on Monday.
North Korea hacked into more than 140,000 computers at 160 South Korean firms and government agencies, planting malicious code under a long-term plan laying groundwork for a massive cyber attack against its rival, police in the South said on Monday.
South Korea has been on heightened alert against cyber attacks by the North after Pyongyang conducted a nuclear test in January and a long-range rocket launch in February that led to new U.N. sanctions. The North has always denied wrongdoing. The hacking began in 2014 and was detected in February, after North Korea managed to steal information from two conglomerates.
Read moreNorth Korea's paranoid computer operating system revealed
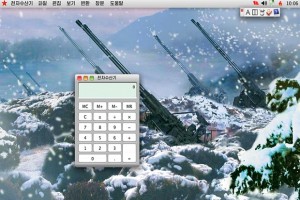 North Korea’s homegrown computer operating system mirrors its political one – marked by a high degree of paranoia and invasive snooping on users, according to two German researchers.
North Korea’s homegrown computer operating system mirrors its political one – marked by a high degree of paranoia and invasive snooping on users, according to two German researchers.
Their investigation, the deepest yet into the country’s Red Star OS, illustrates the challenges Pyongyang faces in trying to embrace the benefits of computing and the internet while keeping a tight grip on ideas and culture. The operating system is not just the pale copy of western ones that many have assumed, said experts of the German IT security company ERNW, who downloaded the software from a website outside North Korea and explored the code in detail.
Read moreDuuzer Trojan: a new backdoor targeting South Korean organizations
 Security researchers at Symantec have uncovered a new Backdoor Trojan that grants hackers remote access and some control over infected machines. "Duuzer," as dubbed by the researchers, has been targeting organizations in South Korea and elsewhere in an attempt to steal valuable information.
Security researchers at Symantec have uncovered a new Backdoor Trojan that grants hackers remote access and some control over infected machines. "Duuzer," as dubbed by the researchers, has been targeting organizations in South Korea and elsewhere in an attempt to steal valuable information.
The Trojan is designed to infect both 32-bit and 64-bit computers running Windows 7, Windows Vista, and Windows XP. It is currently unclear how the malware is being distributed, but according to Symantec Researchers, the most obvious routes are Spear Phishing campaigns and Watering Hole attacks.
Read moreNSA tapped into North Korean networks before Sony attack
 The trail that led American officials to blame North Korea for the destructive cyberattack on Sony Pictures Entertainment winds back to 2010, when the National Security Agency scrambled to break into the computer systems of a country considered one of the most impenetrable targets on earth.
The trail that led American officials to blame North Korea for the destructive cyberattack on Sony Pictures Entertainment winds back to 2010, when the National Security Agency scrambled to break into the computer systems of a country considered one of the most impenetrable targets on earth.
Spurred by growing concern about North Korea’s maturing capabilities, the American spy agency drilled into the Chinese networks that connect North Korea to the outside world, picked through connections in Malaysia favored by North Korean hackers and penetrated directly into the North with the help of South Korea and other American allies.
Read moreWho is behind the Sony Pictures breach?
 The Sony breach certainly seems to be the gift that keeps on giving this holiday season. And if the commonly accepted narrative reflects the truth, this whole nightmare scenario stems from what promised to be a puerile comedy titled “The Interview.”
The Sony breach certainly seems to be the gift that keeps on giving this holiday season. And if the commonly accepted narrative reflects the truth, this whole nightmare scenario stems from what promised to be a puerile comedy titled “The Interview.”
The premise of the movie revolves around a pair of journalists who are granted a rare interview with North Korean supreme leader, Kim Jong-Un, and the subsequent plot to assassinate the Hermit Kingdom’s despotic dictator. Sony, having clearly failed to learn its lesson after attackers hacked its PlayStation Network, is the main character in yet another serious and humiliating security incident.
Read moreNorth Korea accused of hacking smartphones
 South Korea’s National Intelligence Service has alleged that North Korean cyber army has infected a lot of smartphones. Victims reportedly downloaded infected applications from websites assuming that they were games but contained malicious code.
South Korea’s National Intelligence Service has alleged that North Korean cyber army has infected a lot of smartphones. Victims reportedly downloaded infected applications from websites assuming that they were games but contained malicious code.
However, NIS has not revealed whether the infected devices actually suffered any damage. Intelligence officials countered the threat by removing the malicious apps from the infected websites and devices, and securing them with advanced computer vaccines. South Korea has frequently accused North Korea of launching cyber attacks on its tech-savvy citizens, media outlets, and government establishments.
Read more New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
Axarhöfði 14,
110 Reykjavik, Iceland














