Steve Jobs planned 'Holy War' with Google
 Apple founder Steve Jobs was planning to wage a "Holy War" against Google a year before he died, a higly confidential email has revealed.
Apple founder Steve Jobs was planning to wage a "Holy War" against Google a year before he died, a higly confidential email has revealed.
Jobs sent the email in 2010 to his top 100 most senior executives, in which he outlined the company's strategy for the following year.
In it, he announced that 2011 would see a 'Holy War' between Apple and Google, and outlined all the ways in which the two companies would compete – from cloud services to mobile operating systems.
Read moreHacking Into A Tesla Model S Electric Car
 In the modern world though, it typically refers to the process of cracking software codes to take greater control of applications and user interfaces.
In the modern world though, it typically refers to the process of cracking software codes to take greater control of applications and user interfaces.
It's rife in the world of smartphones, and now it's possible with electric vehicles too – such as the technology-heavy Tesla Model S. A central feature of the Model S – literally – is its enormous dashboard-mounted 17-inch touchscreen. It's a technical highlight of the car, allowing owners options from changing simple parameters like cabin temperature, to operating the car's navigation system and infotainment functions. The screen is also a web browser, with all the functions that entails.
Read moreYour favorite Android Apps may have been mining Bitcoin without your knowledge

Researchers said they have uncovered two apps that were downloaded from the official Google Play market more than one million times that use Android devices to mine the Litecoin and Dogecoin cryptocurrencies without explicitly informing end users.
According Trend Micro, a researcher from antivirus provider the apps are Songs, installed from one million to five million times, and Prized, which was installed from 10,000 to 50,000 times. Neither the app descriptions nor their terms of service make clear that the apps subject Android devices to the compute-intensive process of mining, Trend Micro Mobile Threats Analyst Veo Zhang wrote. As of Wednesday afternoon, the apps were still available.
Read moreReplicant developers find and close Samsung Galaxy backdoor
.jpg) "While working on Replicant, a fully free/libre version of Android, we discovered that the proprietary program running on the applications processor in charge of handling the communication protocol with the modem actually implements a backdoor that lets the modem perform remote file I/O operations on the file system", said Replicant developer Paul Kocialkowski.
"While working on Replicant, a fully free/libre version of Android, we discovered that the proprietary program running on the applications processor in charge of handling the communication protocol with the modem actually implements a backdoor that lets the modem perform remote file I/O operations on the file system", said Replicant developer Paul Kocialkowski.
Today's phones come with two separate processors: one is a general-purpose applications processor that runs the main operating system, e.g. Android; the other, known as the modem, baseband, or radio, is in charge of communications with the mobile telephony network. This processor always runs a proprietary operating system, and these systems are known to have backdoors that make it possible to remotely convert the modem into a remote spying device.
Read moreSnowden’s effect or now Twitter wants to “spy” on SMS and calls
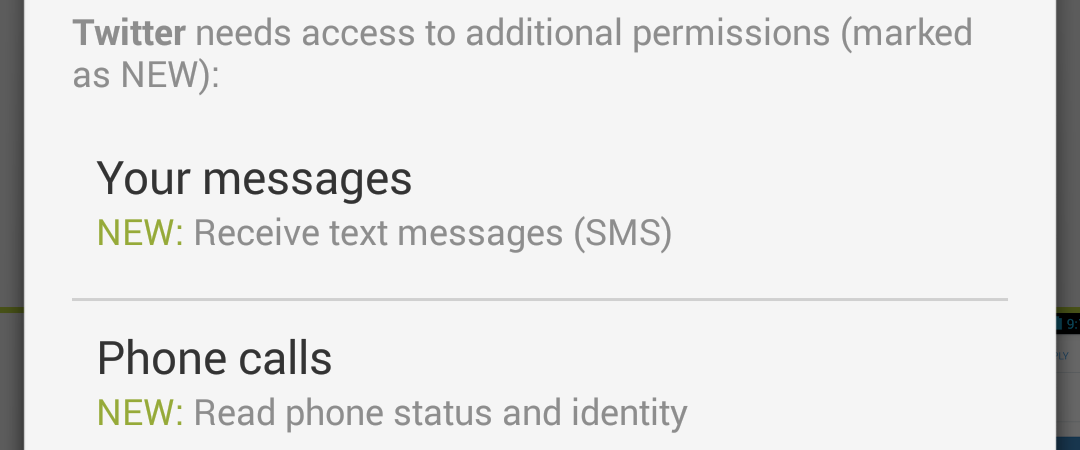 Mobile apps' “appetite” grows for users' private data. Attentive owners of Android may have noticed Twitter’s update request to gain access to SMS and phone status.
Mobile apps' “appetite” grows for users' private data. Attentive owners of Android may have noticed Twitter’s update request to gain access to SMS and phone status.
Previously similar attempts to access SMS have been already observed by Facebook, Viber, Hangouts and Telegram. They would explain such a move with making it easier for users to enter the activation code.
But it gets more difficult to explain this strange desire to access the status of you phone calls. Why would Twitter what to know when and who’s calling?
Read moreSafeUM is now ready for Android OS
 Android is the world's most popular mobile platform. We have finished developing the mobile version application.
Android is the world's most popular mobile platform. We have finished developing the mobile version application.
We designed a clear and easy-to-use interface allowing you to multitask without switching screens.
The application is easy to configure – that will require very little time. Our messenger has been tested on many different devices to find the best color schemes and create a convenient user menu. We took user habits into account and made our application navigation as comfortable and functional as possible. You can customize the menu to your needs just by clicking on one single page.
Read moreAndroid sends plaintext Wi-Fi passwords to Google
 It is possible with the help of "Back up my data" in a mobile operating system. The co-worker of the “Elecontric Frontier Foundation” Micah Lee announced that the function "Back up my data" in OS Android sends passwords from Wi-Fi and private information in plaintext to Google.
It is possible with the help of "Back up my data" in a mobile operating system. The co-worker of the “Elecontric Frontier Foundation” Micah Lee announced that the function "Back up my data" in OS Android sends passwords from Wi-Fi and private information in plaintext to Google.
"Since backup and restore is such a useful feature, and since it's turned on by default, it's likely that the vast majority of Android users are syncing this data with their Google accounts. Because Android is so popular, it's likely that Google has plaintext Wi-Fi passwords for the majority of users,” Lee pointed out.
Read more New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
New secured zone of Google Play: secure messenger SafeUM for Android. Download, Install, Communicate
Axarhöfði 14,
110 Reykjavik, Iceland














