Apple's iOS App Store suffers major attack
 Apple Inc said it is cleaning up its iOS App Store to remove malicious iPhone and iPad programs identified in the first large-scale attack on the popular mobile software outlet.
Apple Inc said it is cleaning up its iOS App Store to remove malicious iPhone and iPad programs identified in the first large-scale attack on the popular mobile software outlet.
The company disclosed the effort after several cyber security firms reported finding a malicious program dubbed XcodeGhost that was embedded in hundreds of legitimate apps. It is the first reported case of large numbers of malicious software programs making their way past Apple's stringent app review process. Prior to this attack, a total of just five malicious apps had ever been found in the App Store, according to cyber security firm Palo Alto Networks Inc.
Read moreIBM warns companies to block Tor network
 IBM is warning companies to stop using the Tor anonymising network and completely block it from corporate networks to avoid being open to increasing ransomware and distributed denial of service attacks.
IBM is warning companies to stop using the Tor anonymising network and completely block it from corporate networks to avoid being open to increasing ransomware and distributed denial of service attacks.
In a new threat intelligence report, IBM says that targeted ransomware is on the rise and that cybercriminals are increasingly making use of the Tor network to mask where the malware came from. Tor is the name for software that anonymises and redirects internet traffic through a worldwide network of relays comprised of volunteers who set up their computers as Tor nodes.
Read moreBitTorrent users can be exploited for DDoS attacks
 Some of the most widely used BitTorrent applications, including uTorrent, Mainline, and Vuze are also the most vulnerable to a newly discovered form of denial of service attack that makes it easy for a single person to bring down large sites.
Some of the most widely used BitTorrent applications, including uTorrent, Mainline, and Vuze are also the most vulnerable to a newly discovered form of denial of service attack that makes it easy for a single person to bring down large sites.
The distributed reflective DoS attacks exploit weaknesses found in the open BitTorrent protocol, which millions of people rely on to exchange files over the Internet. But it turns out that features found uTorrent, Mainline, and Vuze make them especially suitable for the technique. DRDoS allows a single BitTorrent user with only modest amounts of bandwidth to send malformed requests to other BitTorrent users.
Read moreResearchers claim they’ve developed a better, faster Tor
 Tor, the world's largest and most well-known "onion router" network, offers a degree of anonymity that has made it a popular tool of journalists, dissidents, and everyday Internet users who are trying to avoid government or corporate censorship.
Tor, the world's largest and most well-known "onion router" network, offers a degree of anonymity that has made it a popular tool of journalists, dissidents, and everyday Internet users who are trying to avoid government or corporate censorship.
But one thing that it doesn't offer is speed—its complex encrypted "circuits" bring Web browsing and other tasks to a crawl. That means that users seeking to move larger amounts of data have had to rely on virtual private networks—which while they are anonymous, are much less protected than Tor. A group of researchers may have found a new balance between privacy and performance.
Read moreOnline test-takers feel anti-cheating software’s uneasy glare
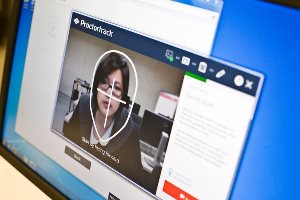 Before Betsy Chao, a senior here at Rutgers University, could take midterm exams in her online courses this semester, her instructors sent emails directing students to download Proctortrack, a new anti-cheating technology.
Before Betsy Chao, a senior here at Rutgers University, could take midterm exams in her online courses this semester, her instructors sent emails directing students to download Proctortrack, a new anti-cheating technology.
Once her exam started, a red warning band appeared on the computer screen indicating that Proctortrack was monitoring her computer and recording video of her. To constantly remind her that she was being watched, the program also showed a live image of her in miniature on her screen. Even for an undergraduate raised in a culture of selfies and Skype, Ms. Chao found the system intrusive.
Read moreTor shutters its anonymous Cloud service
 Tor has announced that it is closing its Cloud Project, which allows users to browse the Web anonymously, effective. The not-for-profit organization said it cannot find enough help to properly maintain its operations and thus bugs in the system have made parts of the service unusable.
Tor has announced that it is closing its Cloud Project, which allows users to browse the Web anonymously, effective. The not-for-profit organization said it cannot find enough help to properly maintain its operations and thus bugs in the system have made parts of the service unusable.
The main reason for discontinuing Tor Cloud is the fact that security software requires maintenance, and Tor Cloud is no exception. There is at least one major bug in the Tor Cloud image that makes it completely dysfunctional, and there are over a dozen other bugs, at least one of them of highest priority.
Read moreBelarus bans Tor and other anonymizers
 Belarus has moved to block access to all Internet anonymizers in the country, including Tor. The country's Communications Ministry published a new decree that mandates how access to certain online resources should be limited by Internet providers at the request of the state. Some of the limitations deal directly with anonymizing services.
Belarus has moved to block access to all Internet anonymizers in the country, including Tor. The country's Communications Ministry published a new decree that mandates how access to certain online resources should be limited by Internet providers at the request of the state. Some of the limitations deal directly with anonymizing services.
The state inspection, upon discovering Internet resources, anonymizing services, that allow Internet users to access online resources whose identifiers are included on the limited access list, will add the identifiers of these Internet resources and anonymizing services to the list as well.
Read moreTor is a big source of bank fraud
 A new report found that a majority of bank account takeovers by cyberthieves over the past decade might have been thwarted had affected institutions known to look for and block transactions coming through Tor, a global communications network that helps users maintain anonymity by obfuscating their true location online.
A new report found that a majority of bank account takeovers by cyberthieves over the past decade might have been thwarted had affected institutions known to look for and block transactions coming through Tor, a global communications network that helps users maintain anonymity by obfuscating their true location online.
The findings come in a non-public report obtained by KrebsOnSecurity that was produced by the Financial Crimes Enforcement Network, a Treasury Department bureau responsible for collecting and analyzing data about financial transactions to combat domestic and international money laundering, terrorist financing and other financial crimes.
Read moreNew point-of-sale malware
 A new kind of point-of-sale malware similar to that which struck Target is being sold in underground markets. The malware was found on VirusTotal, a website where people can submit malware samples to see if one of several dozen security applications detects it.
A new kind of point-of-sale malware similar to that which struck Target is being sold in underground markets. The malware was found on VirusTotal, a website where people can submit malware samples to see if one of several dozen security applications detects it.
It had also been advertised on an underground carding website, where people buy and sell stolen payment card data. Retailers across the USA have been hit hard by malware that scans the volatile memory of computers connected to point-of-sale systems, which handle card payments. It appears to share some of the same source code as Dexter and other characteristics of Chewbacca.
Read moreKickstarter freezes Anonabox privacy router project for misleading funders
 All August Germar asked for fund his privacy-focused router project. But as the attention and controversy around his Kickstarter crowdfunding campaign snowballed over the last five days, he found himself at one point with 82 times that amount—and now with nothing.
All August Germar asked for fund his privacy-focused router project. But as the attention and controversy around his Kickstarter crowdfunding campaign snowballed over the last five days, he found himself at one point with 82 times that amount—and now with nothing.
Kickstarter suspended the crowdfunding campaign for Anonabox, an initiative to sell a tiny router that would run all a user’s online traffic over the anonymity network Tor. The idea tapped into an explosive demand for simple privacy technology. But as funders shoveled more than half a million dollars into the project, they also began to pick apart Anonabox’s claims of creating custom hardware.
Read moreAxarhöfði 14,
110 Reykjavik, Iceland















