EU authorities demand changes from Facebook, Google, Twitter
 Social media companies Facebook Inc, Alphabet Inc and Twitter Inc will have to amend their terms of service for European users within a month or face the risk of fines, a European Commission official said on Friday. U.S. technology companies have faced tight scrutiny in Europe for the way they do business, from privacy to how quickly they remove illegal or threatening content.
Social media companies Facebook Inc, Alphabet Inc and Twitter Inc will have to amend their terms of service for European users within a month or face the risk of fines, a European Commission official said on Friday. U.S. technology companies have faced tight scrutiny in Europe for the way they do business, from privacy to how quickly they remove illegal or threatening content.
The Commission and European consumer protection authorities will "take action to make sure social media companies comply with EU consumer rules," the official said. Germany, the most populous EU state, said this week it planned a new law calling for social networks such as Facebook to remove slanderous or threatening online postings quickly or face fines of up to 50 million euros ($53 million).
Read moreThe NSA's 'Twitter for spies' has over 60,000 users
 Data obtained through a Freedom of Information Act request reveals just how popular the NSA's social network for spies called eChirp really is.
Data obtained through a Freedom of Information Act request reveals just how popular the NSA's social network for spies called eChirp really is.
Last week, the secret-spilling website WikiLeaks made headlines once more for publishing a large cache of alleged secret files about the CIA's hacking operations. Those files apparently came from a little-known service for the US intelligence community known as Intellipedia. Many probably still don't know of the "Wikipedia for spies." And many probably don't know that there's also a Twitter for spies, called eChirp. The service is widely used among American spies.
Read moreFirst Twitter-controlled Android botnet acts as backdoor to download malware
 Security researchers have uncovered the first ever Twitter-controlled Android botnet, which acts as a backdoor to download malware onto infected devices. Dubbed Twitoor, the malicious app is not available on any official Android app stores.
Security researchers have uncovered the first ever Twitter-controlled Android botnet, which acts as a backdoor to download malware onto infected devices. Dubbed Twitoor, the malicious app is not available on any official Android app stores.
Researchers believe that the botnet is possibly distributed via SMS or malicious URLs. The botnet is stealthy and capable of hiding its existence on infected devices. The botnet also masquerades as a porn player app or MMS app but does not come equipped with the functionalities of either. Twitoor has been active for a month and has been downloading several variants of mobile banking malware.
Read moreSpambots have taken over at least 2,500 Twitter accounts
 In the span of two weeks, hackers have broken into more than 2,500 Twitter accounts with large followings, including those of electro-funk duo Chromeo, comedian Azeem Banatwala, football star Cecil Shorts III, and late New York Times journalist.
In the span of two weeks, hackers have broken into more than 2,500 Twitter accounts with large followings, including those of electro-funk duo Chromeo, comedian Azeem Banatwala, football star Cecil Shorts III, and late New York Times journalist.
The hacked accounts were then replaced with bots, and used to tweet links to adult dating sites. The victims had their display names changed, with their profile pictures swapped for pictures of scantily-clad women. While bots are nothing new on Twitter, a platform that’s been plagued with fake accounts for years, this campaign is different because it uses almost exclusively real accounts that got hacked.
Read moreCyber Caliphate hacks 54k Twitter accounts
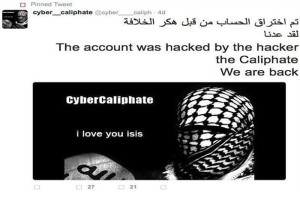 We have discussed several times about the cyber capabilities of the ISIS sympathizers, recently Mikko Hyppönen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages.
We have discussed several times about the cyber capabilities of the ISIS sympathizers, recently Mikko Hyppönen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages.
The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace. Now ISIS hackers are in the headline once again.
Read moreSpy agencies secretly rely on hackers
 The governments of the USA, UK and Canada characterize hackers as a criminal menace, warn of the threats they allegedly pose to critical infrastructure, and aggressively prosecute them, but they are also secretly exploiting their information and expertise, according to top secret documents.
The governments of the USA, UK and Canada characterize hackers as a criminal menace, warn of the threats they allegedly pose to critical infrastructure, and aggressively prosecute them, but they are also secretly exploiting their information and expertise, according to top secret documents.
In some cases, the surveillance agencies are obtaining the content of emails by monitoring hackers as they breach email accounts, often without notifying the hacking victims of these breaches. These revelations about the intelligence agencies’ reliance on hackers are contained in documents provided by Edward Snowden.
Read moreTwitter and Google became partners
 Twitter has struck a deal with Google in order to make its 140-character updates more searchable online. In the first half of this year, tweets will start to be visible in Google’s search results as soon as they’re posted, thanks to a deal giving the Web company access to Twitter’s firehose, the stream of data generated by the microblogging service’s 284 million users.
Twitter has struck a deal with Google in order to make its 140-character updates more searchable online. In the first half of this year, tweets will start to be visible in Google’s search results as soon as they’re posted, thanks to a deal giving the Web company access to Twitter’s firehose, the stream of data generated by the microblogging service’s 284 million users.
Google previously had to crawl Twitter’s site for the information, which will now come automatically from Twitter. Engineers from Twitter and Google are already working on the arrangement. Twitter announced deals to show advertising in Flipboard Inc.’s mobile application.
Read moreBritish hacker linked to attack on Pentagon Twitter feed
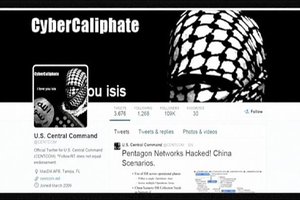 The "CyberCaliphate" hacking group that attacked a Twitter account belonging to the Pentagon was founded by a Briton who was once jailed for hacking the personal address book of former British Prime Minister.
The "CyberCaliphate" hacking group that attacked a Twitter account belonging to the Pentagon was founded by a Briton who was once jailed for hacking the personal address book of former British Prime Minister.
U.S. and European government sources said investigators strongly believe that the hacker was the leader of CyberCaliphate, though they do not know if he was personally involved in hacking the Twitter and YouTube accounts of the U.S. Central Command, which oversees military operations in the Middle East. He could not be reached for comment. Pentagon spokesman has called the cyberattack "inconvenient".
Read moreShould you let your kids on Facebook or Twitter?
 You can tell your kids to stay off the social networks and you can tell yourself that they’ll listen, but chances are they’ll find a way on, anyway. So we’re going to address reality and do our best to ensure that their Facebook and Twitter accounts are secure and private and that they use the networks as safely and responsibly as possible.
You can tell your kids to stay off the social networks and you can tell yourself that they’ll listen, but chances are they’ll find a way on, anyway. So we’re going to address reality and do our best to ensure that their Facebook and Twitter accounts are secure and private and that they use the networks as safely and responsibly as possible.
Of course, Twitter and Facebook are data brokers. This means they make money selling anything and everything you post there to third-party marketing and advertising firms. It’s also safe to assume they are tracking any web-browsing you do while logged in, but you can at least try to prevent this.
Read moreGoogle to revamp its products with 12-and-younger focus
 With Google processing 40,000 search queries a second — or 1.2 trillion a year — it's a safe bet that many of those doing the Googling are kids. Little surprise then that beginning next year the tech giant plans to create specific versions of its most popular products for those 12 and younger.
With Google processing 40,000 search queries a second — or 1.2 trillion a year — it's a safe bet that many of those doing the Googling are kids. Little surprise then that beginning next year the tech giant plans to create specific versions of its most popular products for those 12 and younger.
The most likely candidates are those that are already popular with a broad age group, such as search, YouTube and Chrome. Google would not offer a timetable for the rollout. Google wants to be thoughtful about what we do, giving parents the right tools to oversee their kids' use products. So the better approach is to simply see to it that the tech is used in a better way.
Read moreAxarhöfði 14,
110 Reykjavik, Iceland















