Twitter security tips
 The concept is simple: all posts must be limited to 140 characters maximum. Despite it’s simple concept, the site sure has grown. The simple idea of Twitter has allowed it to average over 305 million active monthly users, which makes it one of the most popular social media platforms.
The concept is simple: all posts must be limited to 140 characters maximum. Despite it’s simple concept, the site sure has grown. The simple idea of Twitter has allowed it to average over 305 million active monthly users, which makes it one of the most popular social media platforms.
However as with all sites with gigantic user bases, cyber-criminals see an opportunity to make a profit. As a result, it is important to ensure that you keep your account as safe and protected as it can possibly be. Here are some tips to follow to keep your Twitter account safe and secure. As we’ve mentioned many times before, a good password is vital to any private account you may have.
Read moreTwitter warns over potential state-sponsored hack
 Twitter has issued its first ever warning about a possible hack by state-sponsored actors, as the social media site steps up its scrutiny of possible security breaches.
Twitter has issued its first ever warning about a possible hack by state-sponsored actors, as the social media site steps up its scrutiny of possible security breaches.
The alert highlights growing concern over hacking activity backed by foreign governments after a year in which high-profile cyber attacks included the breach of 22m personnel profiles at the US Department of Homeland Security. Google and Facebook already have warning systems to alert users who may be targeted by state-sponsored hackers. Twitter sent a warning email to users who may have been affected, stating that the hackers may have been trying to obtain phone numbers, email addresses, and IP addresses.
Read moreTwitter will finally start making money off people without Twitter accounts
 This is the moment Twitter investors have been waiting for. Twitter announced Thursday that it will start showing ads to its “logged out” audience, a group of roughly 500 million people who visit Twitter every month but who don’t have active user accounts.
This is the moment Twitter investors have been waiting for. Twitter announced Thursday that it will start showing ads to its “logged out” audience, a group of roughly 500 million people who visit Twitter every month but who don’t have active user accounts.
That means if you click on a tweet that appears in a Google search, for instance, you may see ads on that tweet page or on the tweet creator’s profile. This is a huge deal for Twitter. First, it’s important to some advertisers, who don’t think Twitter has enough registered users — especially compared to Facebook — to matter, and also to Wall Street, for the same reasons.
Read moreCyber Caliphate hacks 54k Twitter accounts
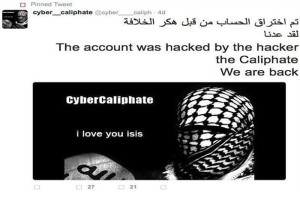 We have discussed several times about the cyber capabilities of the ISIS sympathizers, recently Mikko Hyppönen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages.
We have discussed several times about the cyber capabilities of the ISIS sympathizers, recently Mikko Hyppönen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages.
The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace. Now ISIS hackers are in the headline once again.
Read moreFake Bloomberg report spikes Twitter shares
 A fake news report purportedly from Bloomberg about a possible $31 billion takeover of Twitter spurred a five percent surge in the social network's shares Tuesday before it was denied.
A fake news report purportedly from Bloomberg about a possible $31 billion takeover of Twitter spurred a five percent surge in the social network's shares Tuesday before it was denied.
The report appeared on a Bloomberg.market web page virtually identical to the powerful financial news agency's real pages at Bloomberg.com, and with links to other real Bloomberg reports. The fake report said Twitter "is working closely with bankers after receiving an offer to be bought out for $31 billion," citing, as news agencies frequently do in such reports, "people with knowledge of the situation." The story was fake.
Read moreFake Twitter verification profiles trick victims into sharing personal, payment card info
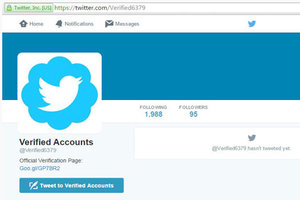 A lot of Twitter users looking for a way to get their accounts verified have been duped by a single fake account promising to provide the service into visiting a phishing page.
A lot of Twitter users looking for a way to get their accounts verified have been duped by a single fake account promising to provide the service into visiting a phishing page.
How many of them actually went through the steps required is unknown, but according to Malwarebytes' Chris Boyd, this wasn't the only account of this kind to be suspended recently, and there are sure to be others popping up. The account in question successfully impersonated Twitter's official "Verified Account" account. The phishers used the same name and icon but, of course, couldn't get the blue badge with a check mark next to the username.
Read moreTwitter has new plans: your life is not a secret anymore
 Computer systems are already aggregating trillions of tweets from the microblogging site, sorting and sifting through countless conversations, following the banter and blustering, ideas and opinions of users in search of commercial opportunities.
Computer systems are already aggregating trillions of tweets from the microblogging site, sorting and sifting through countless conversations, following the banter and blustering, ideas and opinions of users in search of commercial opportunities.
In Twitter data strategy chief’s vision of the future, companies surprising their customers like this could become an everyday occurrence – made possible because Twitter is listening. It is not only commercial interests that are mining the data. Google and Facebook have built their businesses around sharing data, but their control of our private information have become a source of huge controversy.
Read moreSpy agencies secretly rely on hackers
 The governments of the USA, UK and Canada characterize hackers as a criminal menace, warn of the threats they allegedly pose to critical infrastructure, and aggressively prosecute them, but they are also secretly exploiting their information and expertise, according to top secret documents.
The governments of the USA, UK and Canada characterize hackers as a criminal menace, warn of the threats they allegedly pose to critical infrastructure, and aggressively prosecute them, but they are also secretly exploiting their information and expertise, according to top secret documents.
In some cases, the surveillance agencies are obtaining the content of emails by monitoring hackers as they breach email accounts, often without notifying the hacking victims of these breaches. These revelations about the intelligence agencies’ reliance on hackers are contained in documents provided by Edward Snowden.
Read moreTwitter and Google became partners
 Twitter has struck a deal with Google in order to make its 140-character updates more searchable online. In the first half of this year, tweets will start to be visible in Google’s search results as soon as they’re posted, thanks to a deal giving the Web company access to Twitter’s firehose, the stream of data generated by the microblogging service’s 284 million users.
Twitter has struck a deal with Google in order to make its 140-character updates more searchable online. In the first half of this year, tweets will start to be visible in Google’s search results as soon as they’re posted, thanks to a deal giving the Web company access to Twitter’s firehose, the stream of data generated by the microblogging service’s 284 million users.
Google previously had to crawl Twitter’s site for the information, which will now come automatically from Twitter. Engineers from Twitter and Google are already working on the arrangement. Twitter announced deals to show advertising in Flipboard Inc.’s mobile application.
Read moreAvoiding scams and trolls on Twitter
 Not long ago, Twitter was a novelty social media site that average users thought was silly. Now the microblogging tool is a vital news source and publishing platform, letting anyone share information and opinions from almost anywhere. Almost everyone is on it now, from your favorite celebrity to your parents.
Not long ago, Twitter was a novelty social media site that average users thought was silly. Now the microblogging tool is a vital news source and publishing platform, letting anyone share information and opinions from almost anywhere. Almost everyone is on it now, from your favorite celebrity to your parents.
But as is the case with every emergent trend on the Internet, Twitter is also populated by scammers and so-called ‘trolls,’ people who harass and provoke others with posts that range from the annoying to the profane. And what’s more, that security risk is essentially built into Twitter — its public-facing nature allows anyone to follow or mention anyone else.
Read moreAxarhöfði 14,
110 Reykjavik, Iceland















